Deploying an Application Using 3-Tier Architecture on AWS 🚀: A Step-by-Step Guide
Table of contents
- Step 1: Setting Up the Infrastructure 🌐
- Step 2: Configuring Security Groups🔒
- Step 3: Creating the Database server 🗃️
- Step 4: Creating the Servers for frontend and backend Applications 💻
- Step 5: Setting up Database 🗃️
- Step 6: Deploying the Backend Application 🐳
- Step 7: Setting Up Load Balancer and Auto Scaling For Backend application ⚖️
- Step 8: Deploying the Frontend Application 🐳
- Step 9: Setting Up Load Balancer and Auto Scaling For Frontend application ⚖️
- Step 10: Accessing the Application 🌐
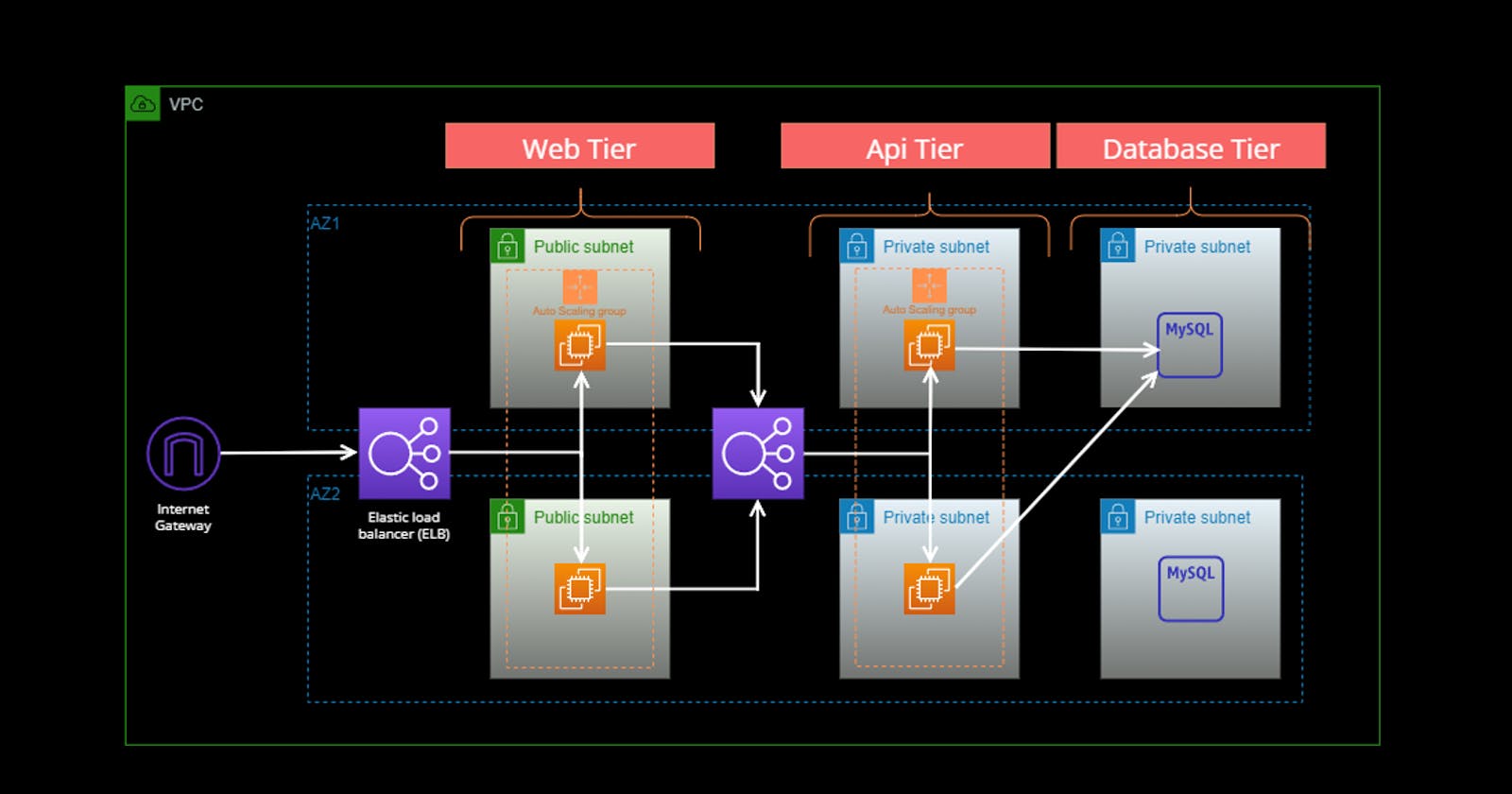
In this guide, we will walk you through the process of deploying an application using a 3-tier architecture on AWS . This architecture separates the first layer is frontend application, Second layer is backend application and the third layer is database for improved scalability and maintainability of the application. We will utilize various AWS services such as VPC, EC2, RDS, Auto Scaling, and Application Load Balancer to achieve our deployment.
Step 1: Setting Up the Infrastructure 🌐
Creating a Virtual Private Cloud (VPC):
Navigate to the AWS Management Console and create a new VPC.
name - "vpc-for-3tier"
IPv4 CIDR block - "10.0.0.0/20"
Click on "Create VPC"
Creating Subnets:
Create the following subnets within the VPC:
VPC ID - "vpc-for-3tier"
Subnet Setting:
Subnet 1(subnet for frontend application ec2):-
Name: public-subnet-1, Availability Zone: us-east-1a, CIDR: 10.0.1.0/24
Subnet 2(subnet for frontend application ec2):-
Name: public-subnet-2, Availability Zone: us-east-1b, CIDR: 10.0.2.0/24
Subnet 3(subnet for backend application ec2):-
Name: private-subnet-1, Availability Zone: us-east-1a, CIDR: 10.0.3.0/24
Subnet 4(subnet for backend application ec2):-
Name: private-subnet-1, Availability Zone: us-east-1b, CIDR: 10.0.4.0/24
Subnet 5(subnet for Database):-
Name: db-subnet-1, Availability Zone: us-east-1a, CIDR: 10.0.5.0/24
Subnet 6(subnet for Database):-
Name: db-subnet-2, Availability Zone: us-east-1b, CIDR: 10.0.6.0/24
Click on "Create subnet"
Setting Up Internet Gateway (IGW):
Create an Internet Gateway.
Name tag - "My-IG"
Click on "Create internet Gateway"
Select Internet Gateway "My-IG" and click on "Attach to vpc"
Select vpc - "vpc-for-3tier"
Click on "Attach internet Gateway"
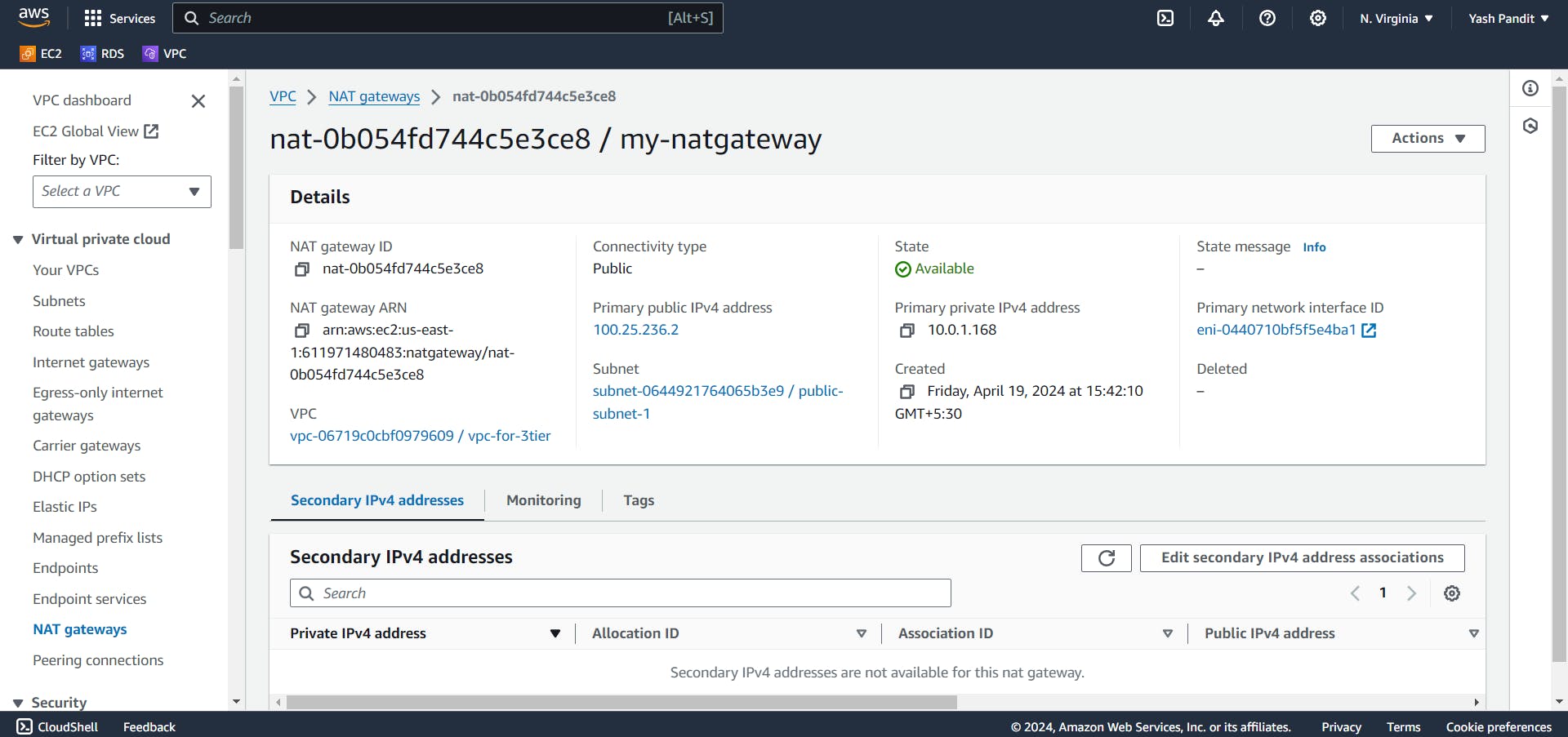
Creating a NAT Gateway :
Create an NAT Gateway.
Name - "my-natgateway"
Subnet - "public-subnet-1"
Connectivity type - "Public"
Click on "Allocate Elastic IP"
Click on "Create"
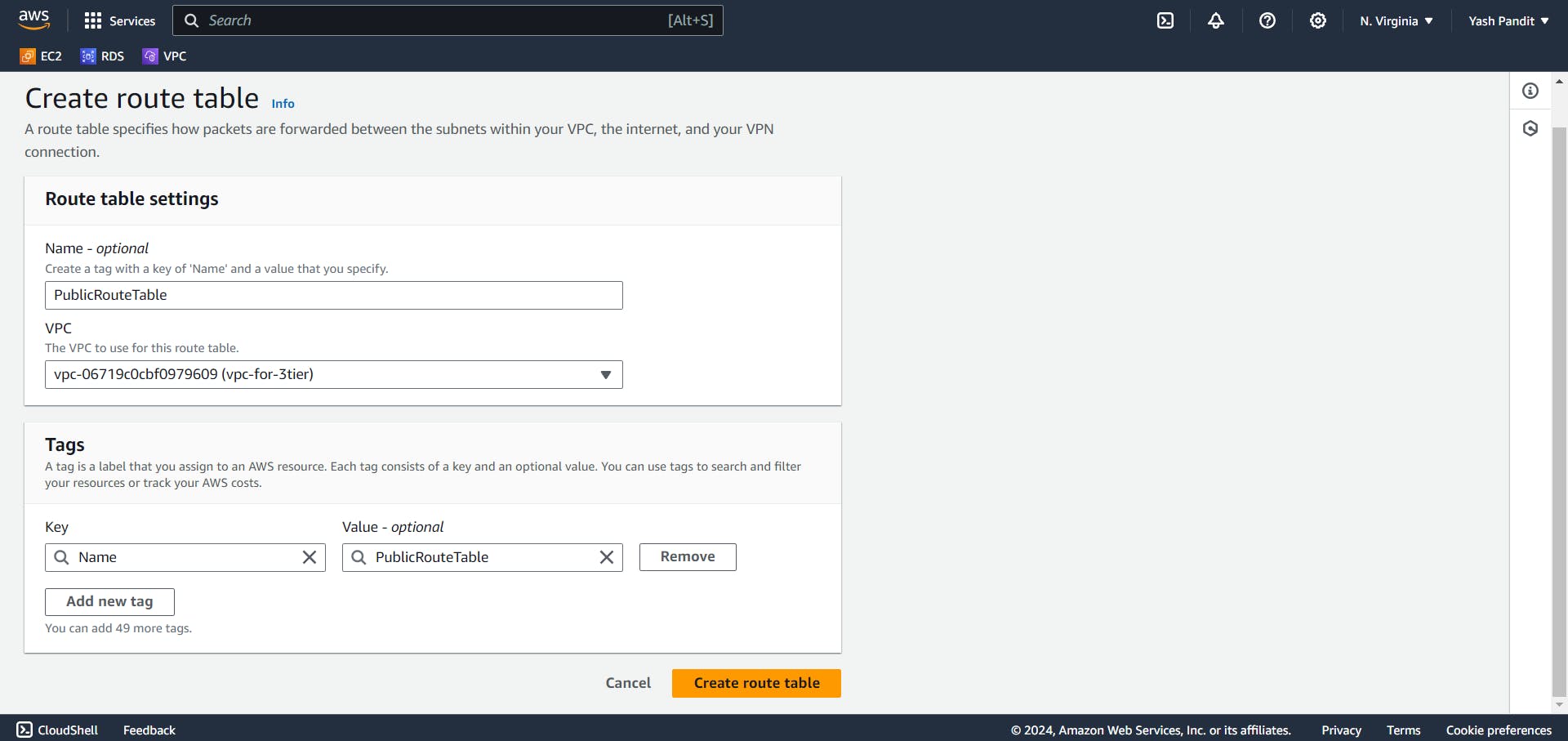
Configuring Route Tables:
Create a route table for public subnets.
Name -"PublicRouteTable"
VPC -"vpc-for-3tier"
Click on -"Create route table"
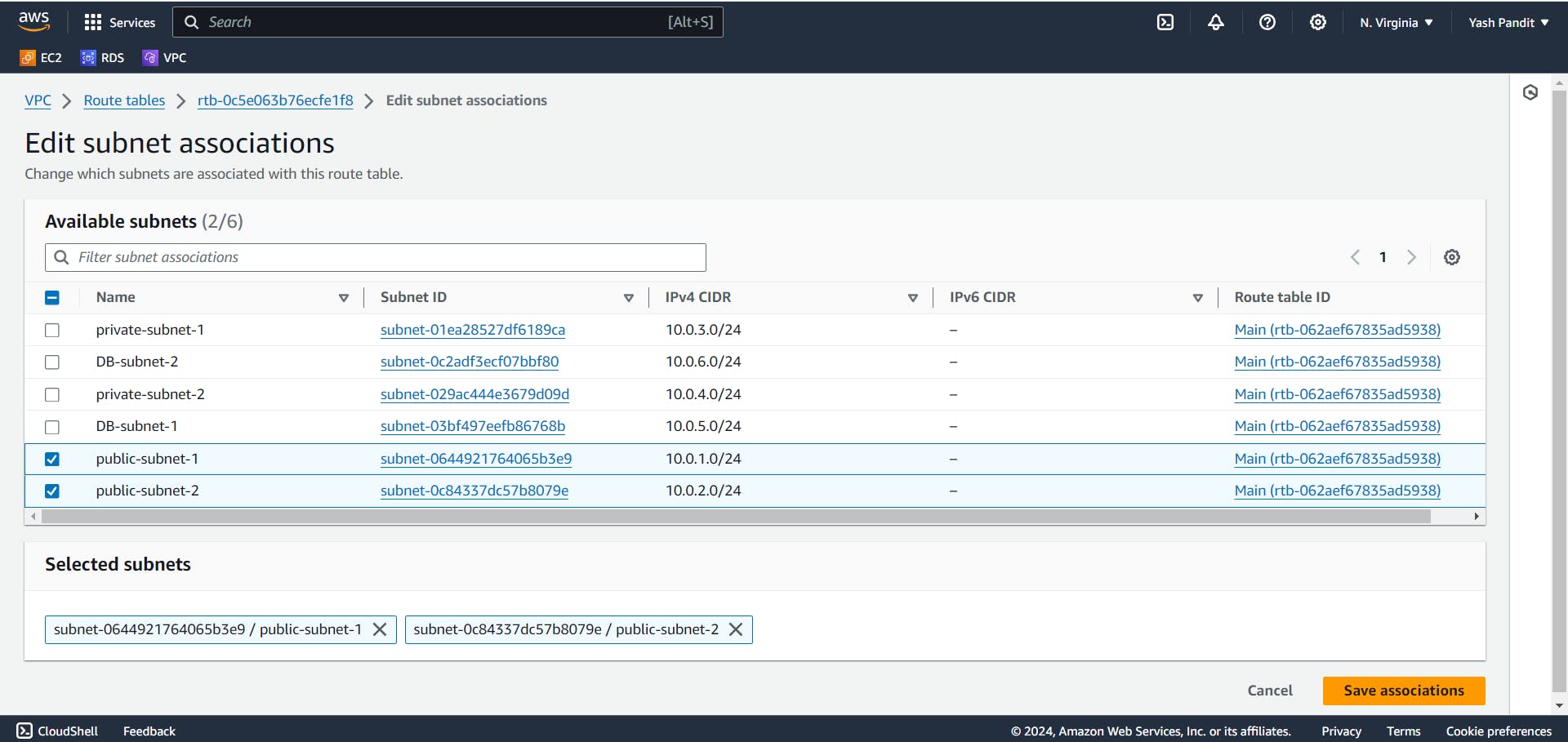
Associate the route table with public subnets:-
Click on "Actions" select "Edit subnet associations"
In "Available subnets" select "public-subnet-1" and "public-subnet-2"
Click on "Save associations"
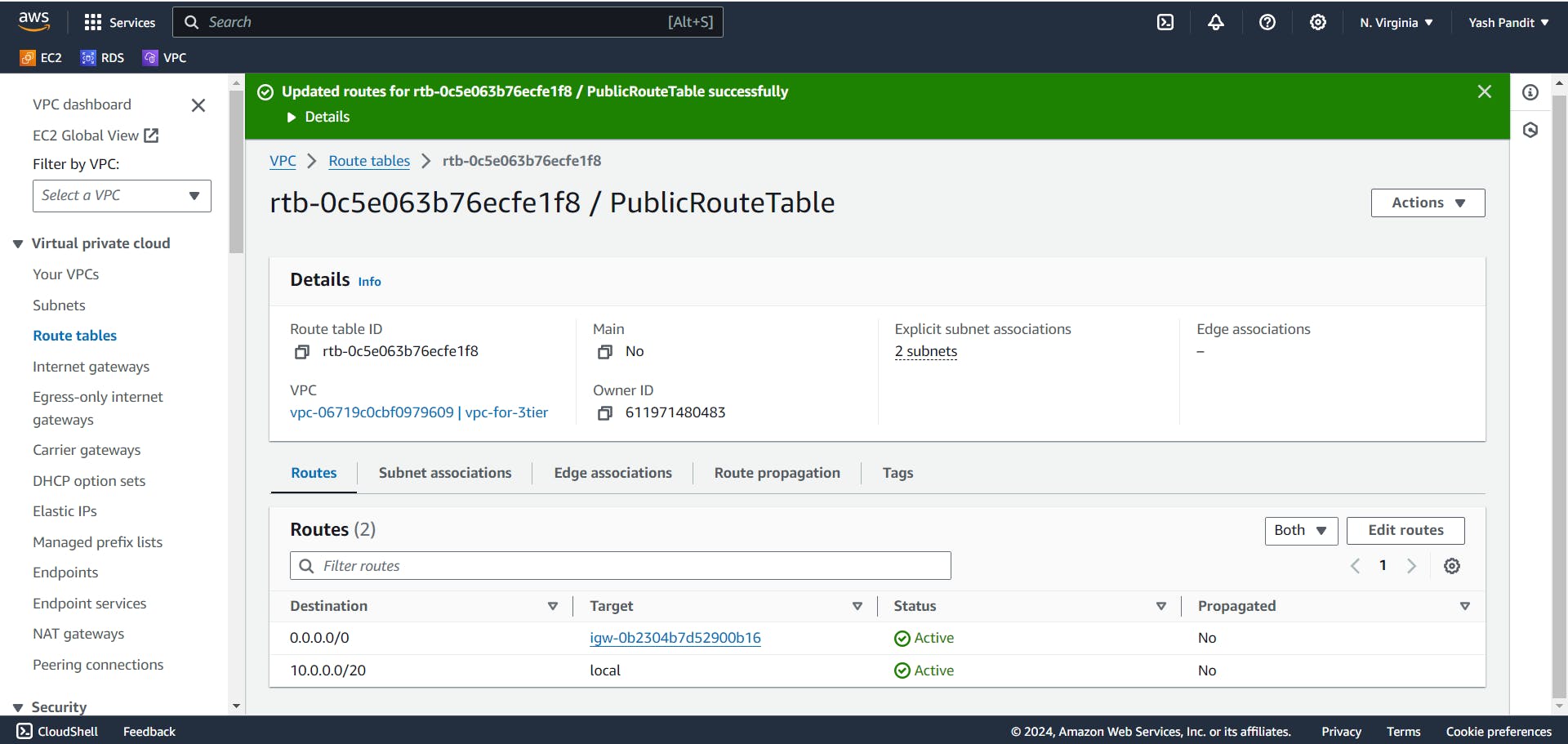
Add a route with destination "0.0.0.0/0" pointing to the Internet Gateway "My-IG" :-
Click on "Edit routes"
In "Edit routes" click on "Add routes"
destination - "0.0.0.0/0" , Target - "My-IG"
Click on "Save changes"
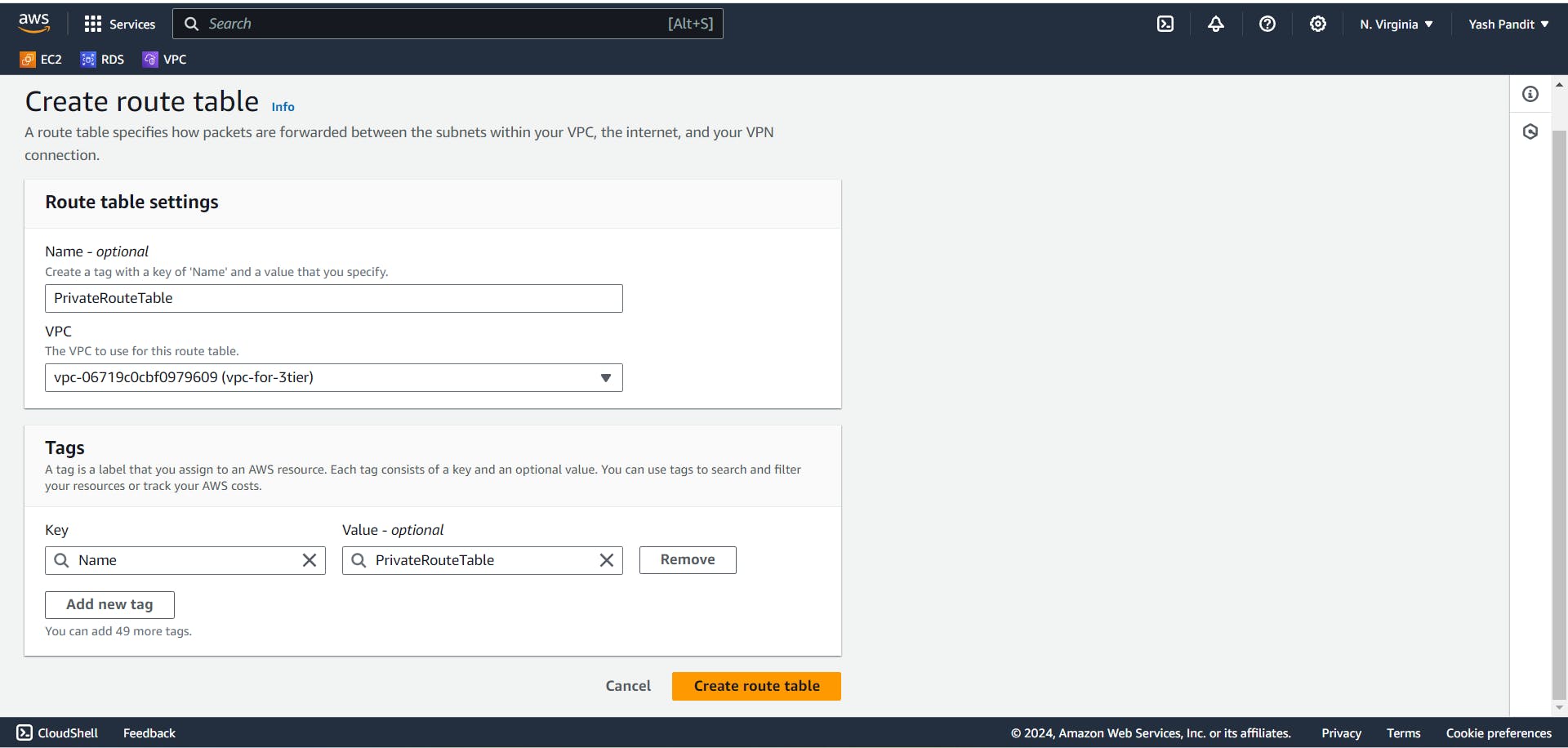
Create a route table for Private subnets.
Name -"PrivateRouteTable"
VPC -"vpc-for-3tier"
Click on -"Create route table"
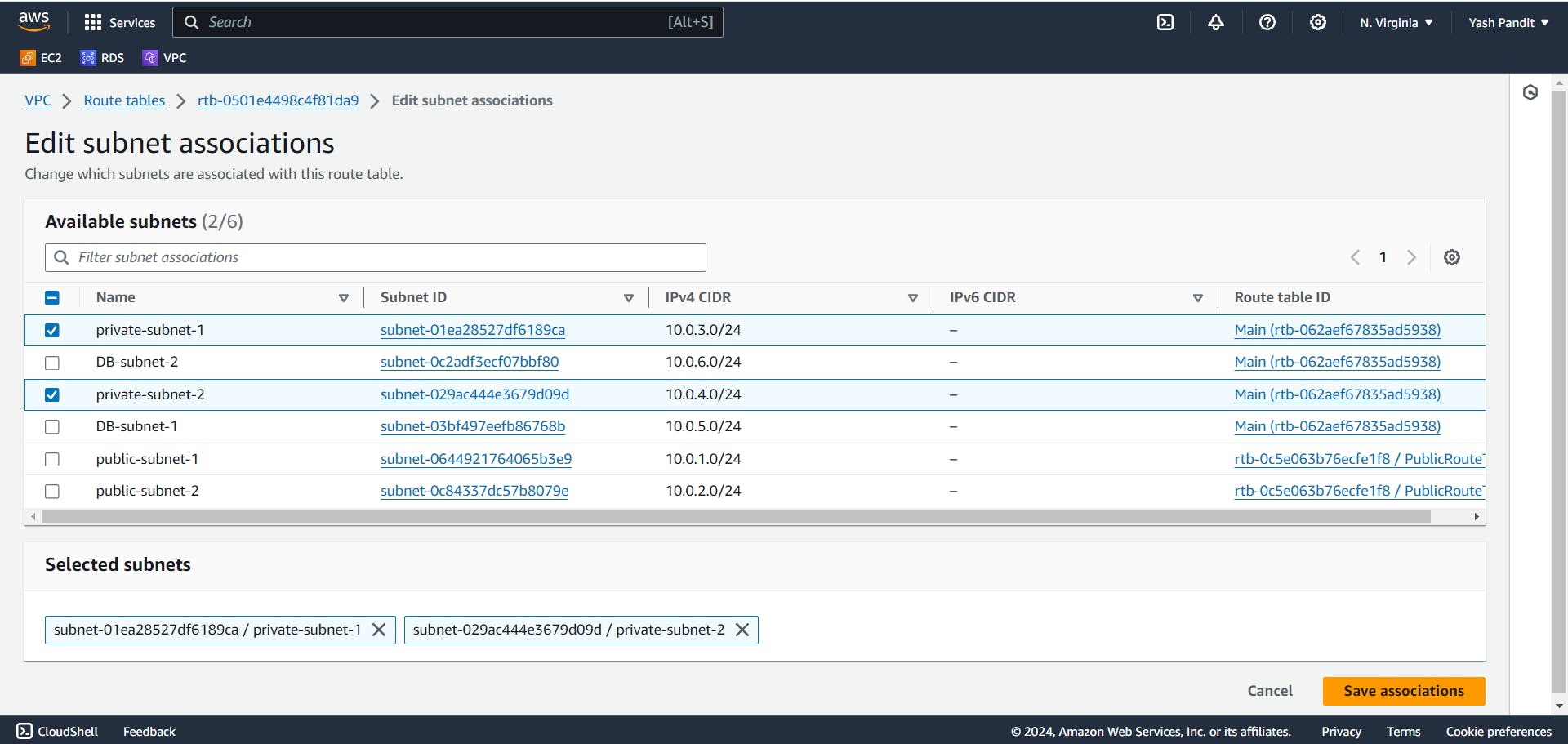
Associate the route table with public subnets:-
Click on "Actions" select "Edit subnet associations"
In "Available subnets" select "private-subnet-1" and "private-subnet-2"
Click on "Save associations"
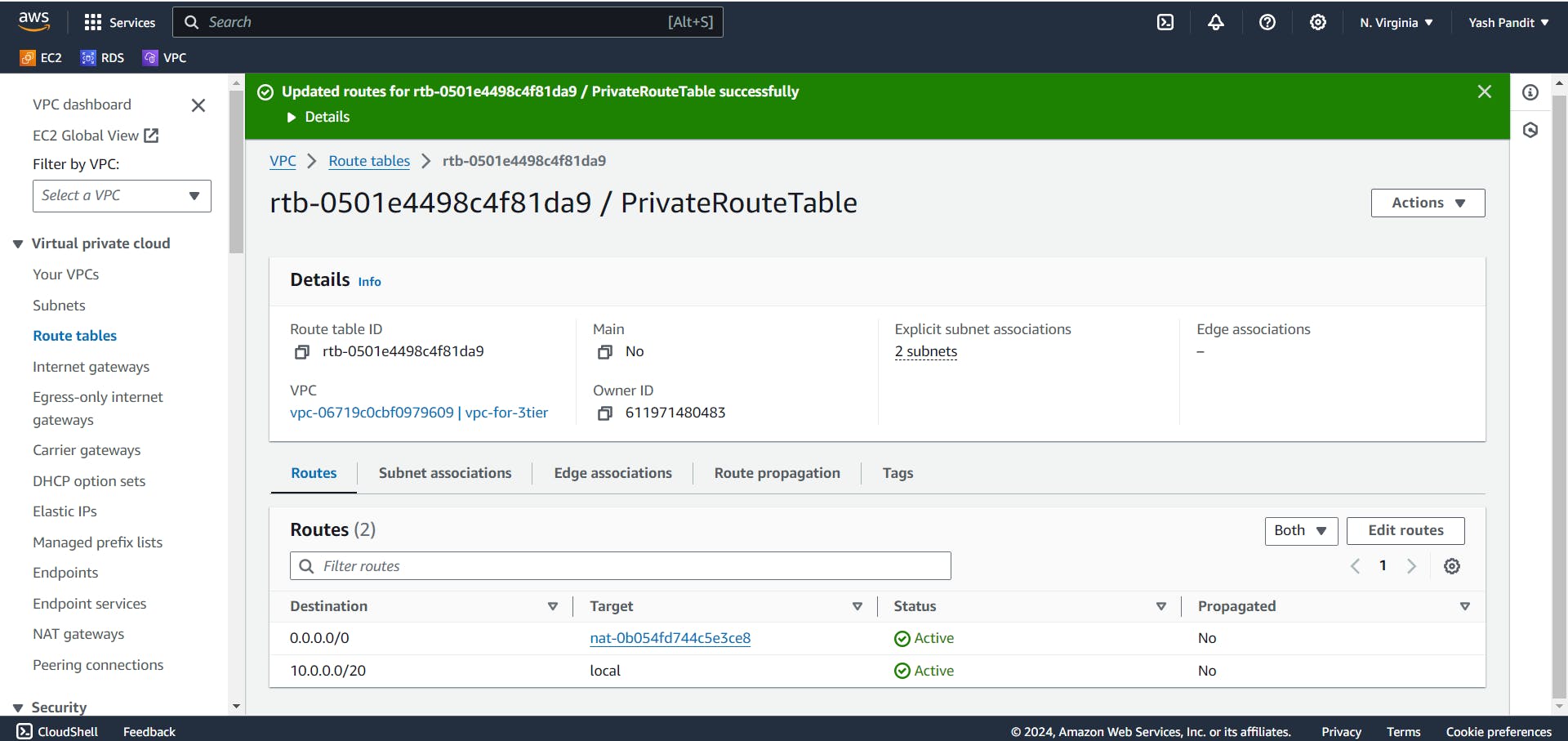
Add a route with destination "0.0.0.0/0" pointing to the NAT Gateway "my-natgateway" :-
Click on "Edit routes"
In "Edit routes" click on "Add routes"
destination - "0.0.0.0/0" , Target - "my-natgateway"
Click on "Save changes"
Step 2: Configuring Security Groups🔒
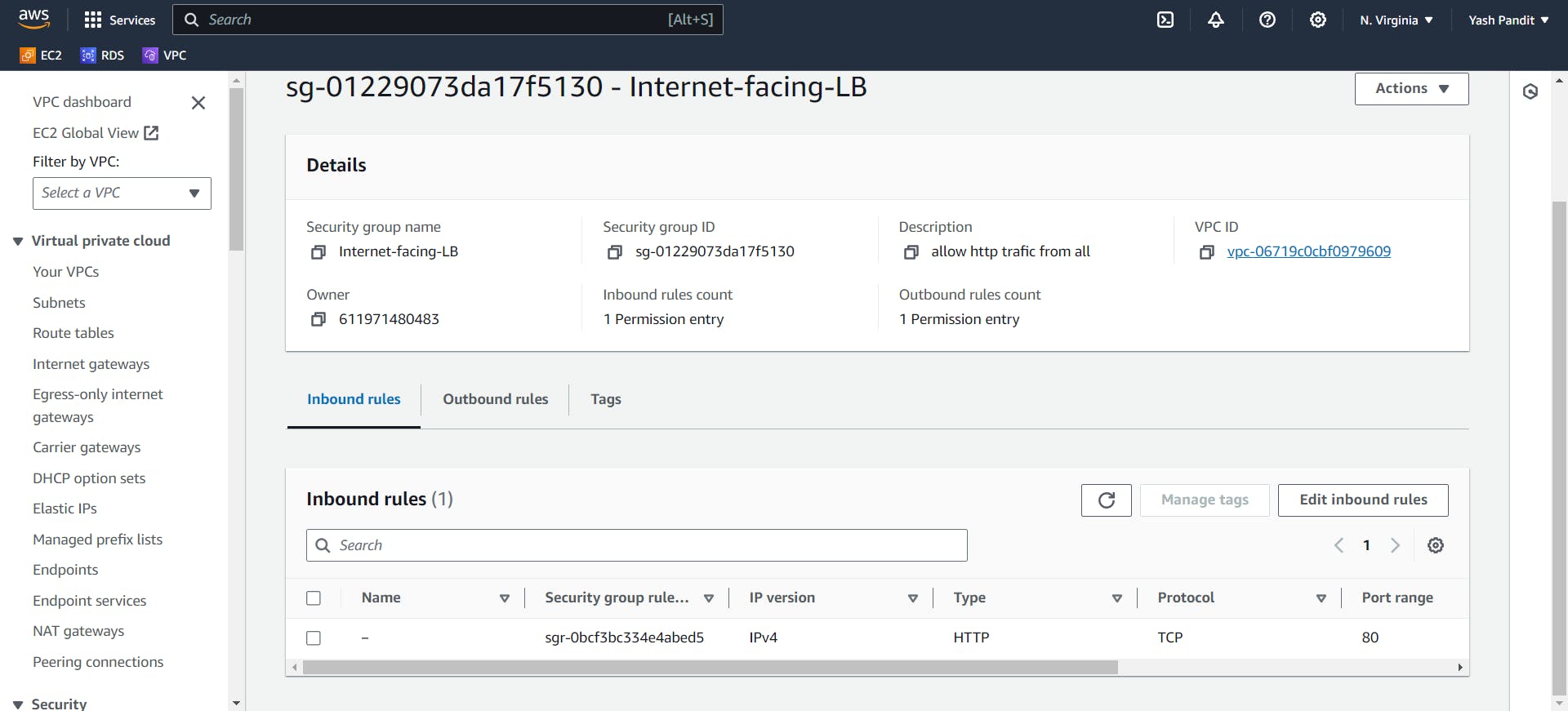
Load Balancer Security Group for Internet facing load balancer (Internet-facing-LB):
Click on "Create security group"
Security group name - "Internet-facing-LB"
VPC - "vpc-for-3tier"
Allow inbound HTTP traffic (Port 80) from anywhere:-
Type - "HTTP", Source - "0.0.0.0/0"
Allow all outbound traffic:-
Type - "All traffic" , Destination - "0.0.0.0/0"
Click on "Create security group"
Web Server Security Group for frontend application ec2 (Web-SG):
Click on "Create security group"
Security group name - "Web-SG"
VPC - "vpc-for-3tier"
Allow inbound HTTP traffic (Port 80) from Load Balancer Security Group and Allow SSH traffic (Port 22) from anywhere for administrative access:-
Type - "HTTP", Source - "Internet-facing-LB"
Click on "Add rule"
Type - "SSH", Source - "0.0.0.0/0"
Allow all outbound traffic:-
Type - "All traffic" , Destination - "0.0.0.0/0"
Click on "Create security group"
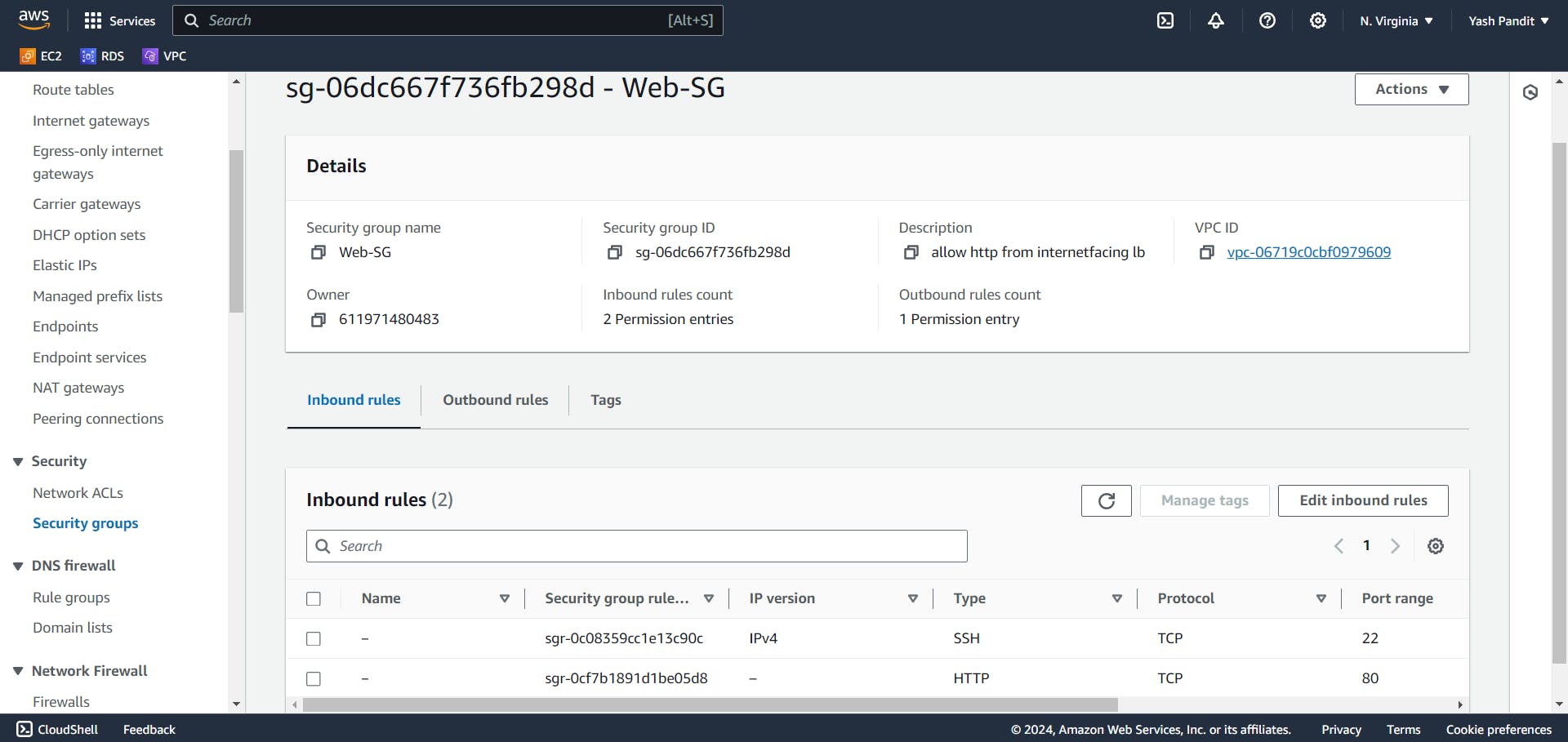
Load Balancer Security Group for internal load balancer (Internal-LB):
Click on "Create security group"
Security group name - "Internal-LB"
VPC - "vpc-for-3tier"
Allow inbound HTTP traffic (Port 80) from Web-SG:-
Type - "HTTP", Source - "Web-SG"
Allow all outbound traffic:-
Type - "All traffic" , Destination - "0.0.0.0/0"
Click on "Create security group"
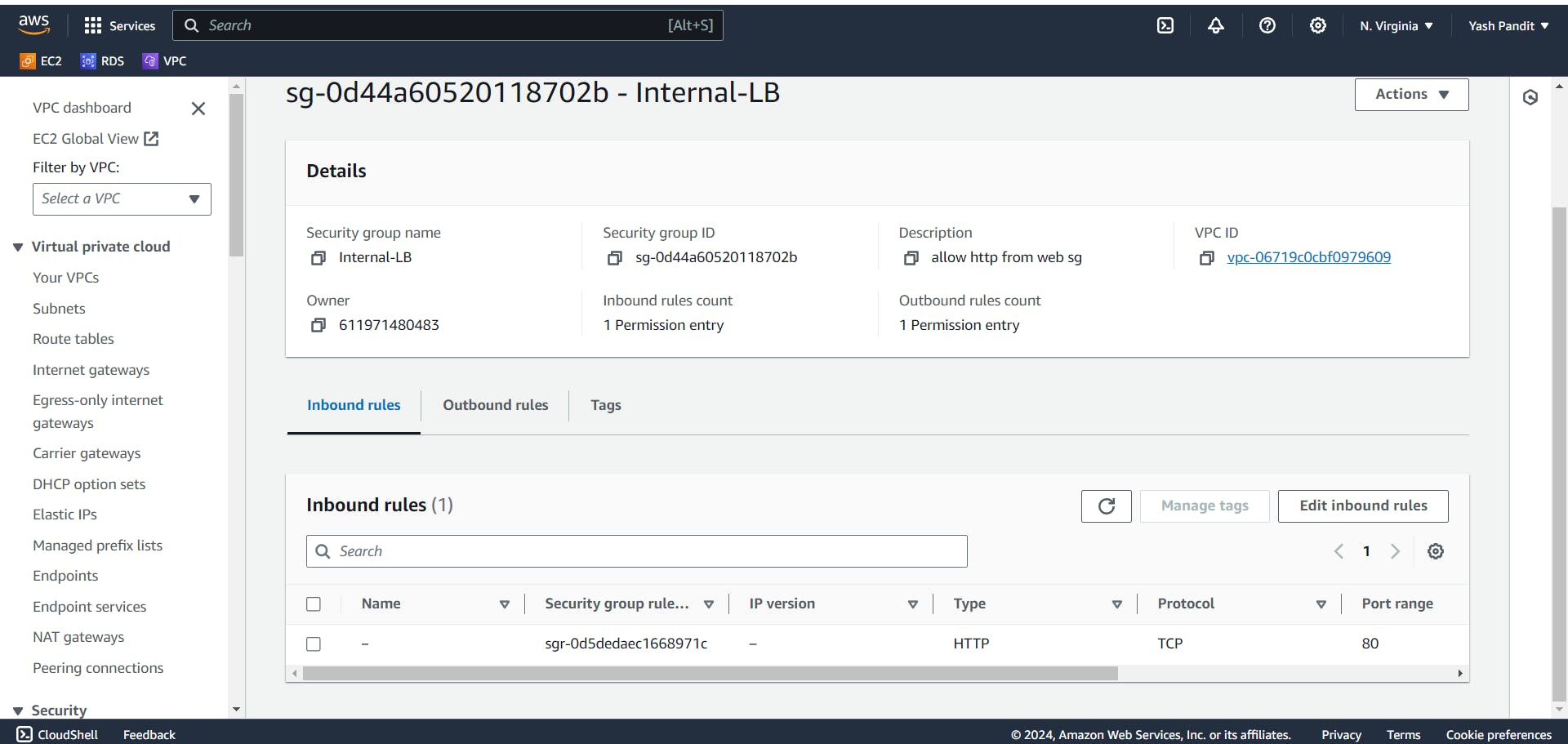
API Server Security Group for backend application ec2(Api-SG):
Click on "Create security group"
Security group name - "Api-SG"
VPC - "vpc-for-3tier"
Allow inbound Custom traffic (Port 5000) from Internal Load Balancer Security Group and Allow SSH traffic (Port 22) from Web-SG for administrative access:-
Type - "Custom", Port range- "5000", Source - "Internal-LB"
Click on "Add rule"
Type - "SSH", Source - "Web-SG"
Allow all outbound traffic:-
Type - "All traffic" , Destination - "0.0.0.0/0"
Click on "Create security group"
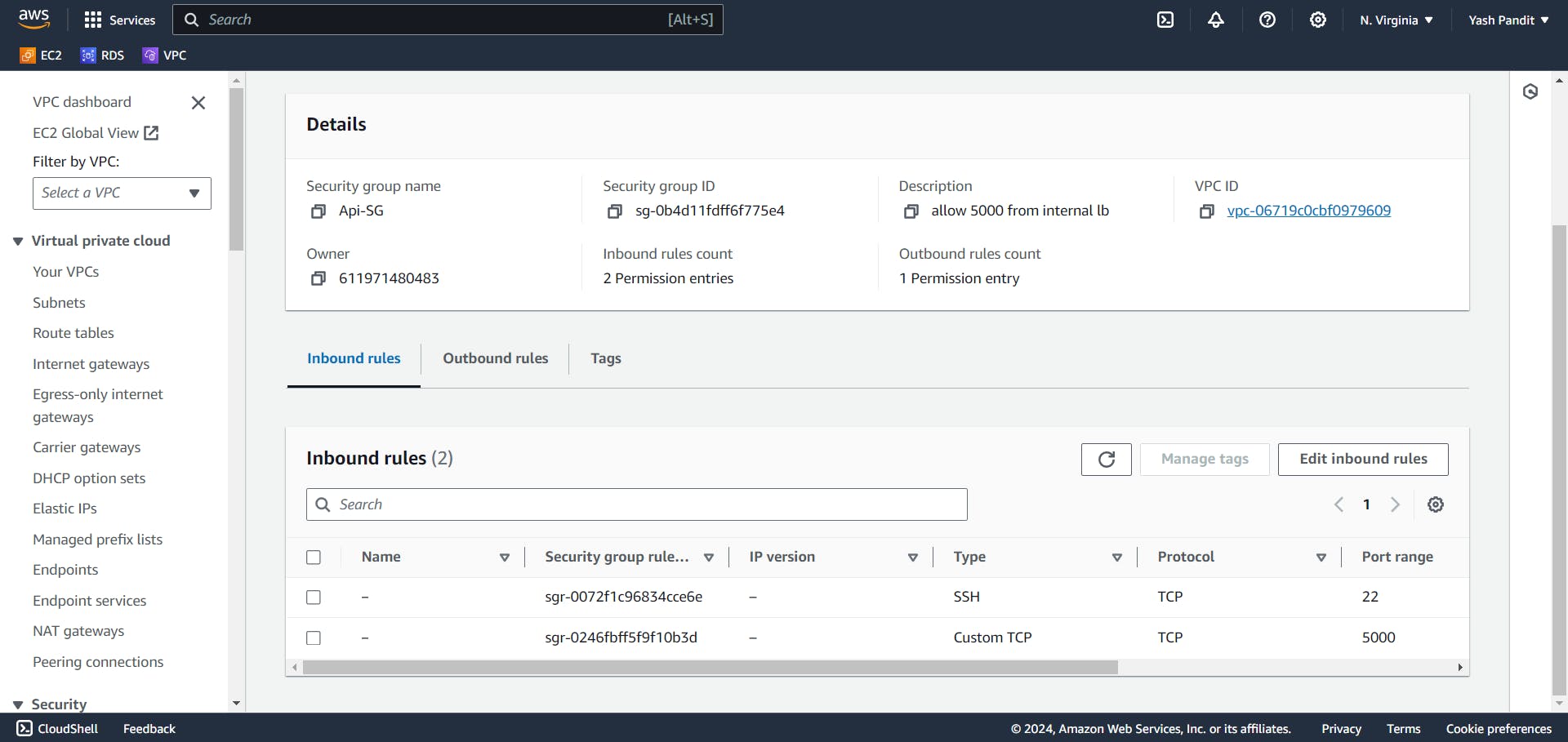
Database Server Security Group (DB-SG):
Click on "Create security group"
Security group name - "DB-SG"
VPC - "vpc-for-3tier"
Allow inbound MySQL traffic (Port 3306) from Api Server Security Group:-
Type - "MYSQL/Aurora", Source - "Api-SG"
Allow all outbound traffic.
Type - "All traffic" , Destination - "0.0.0.0/0"
Click on "Create security group"
Step 3: Creating the Database server 🗃️
Creating a Database Subnet Group:
Go to Amazon RDS and select "Subnet groups".
Click on "Create DB Subnet Group"
Name - "three-tier-subnet-group"
VPC - "vpc-for-3tier"
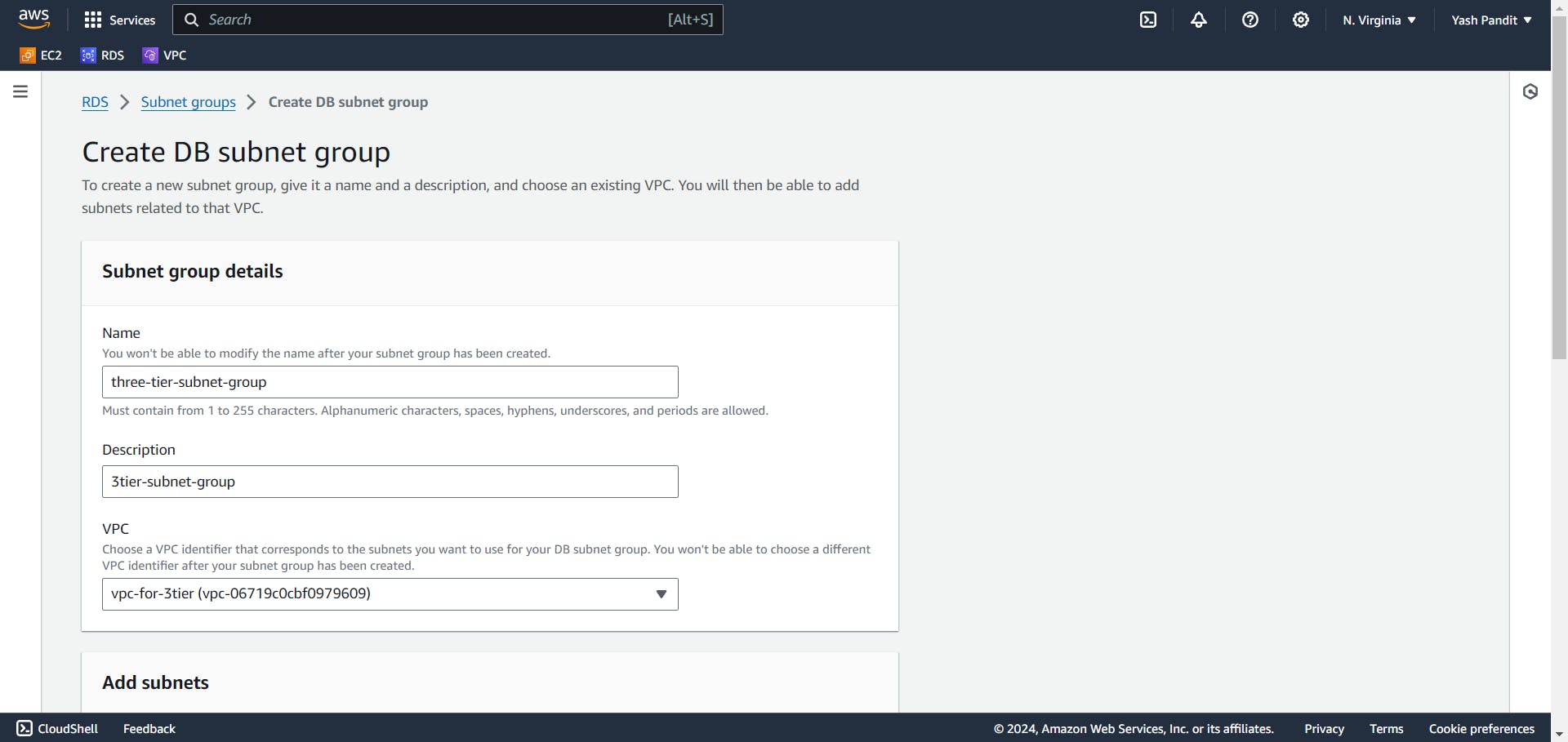
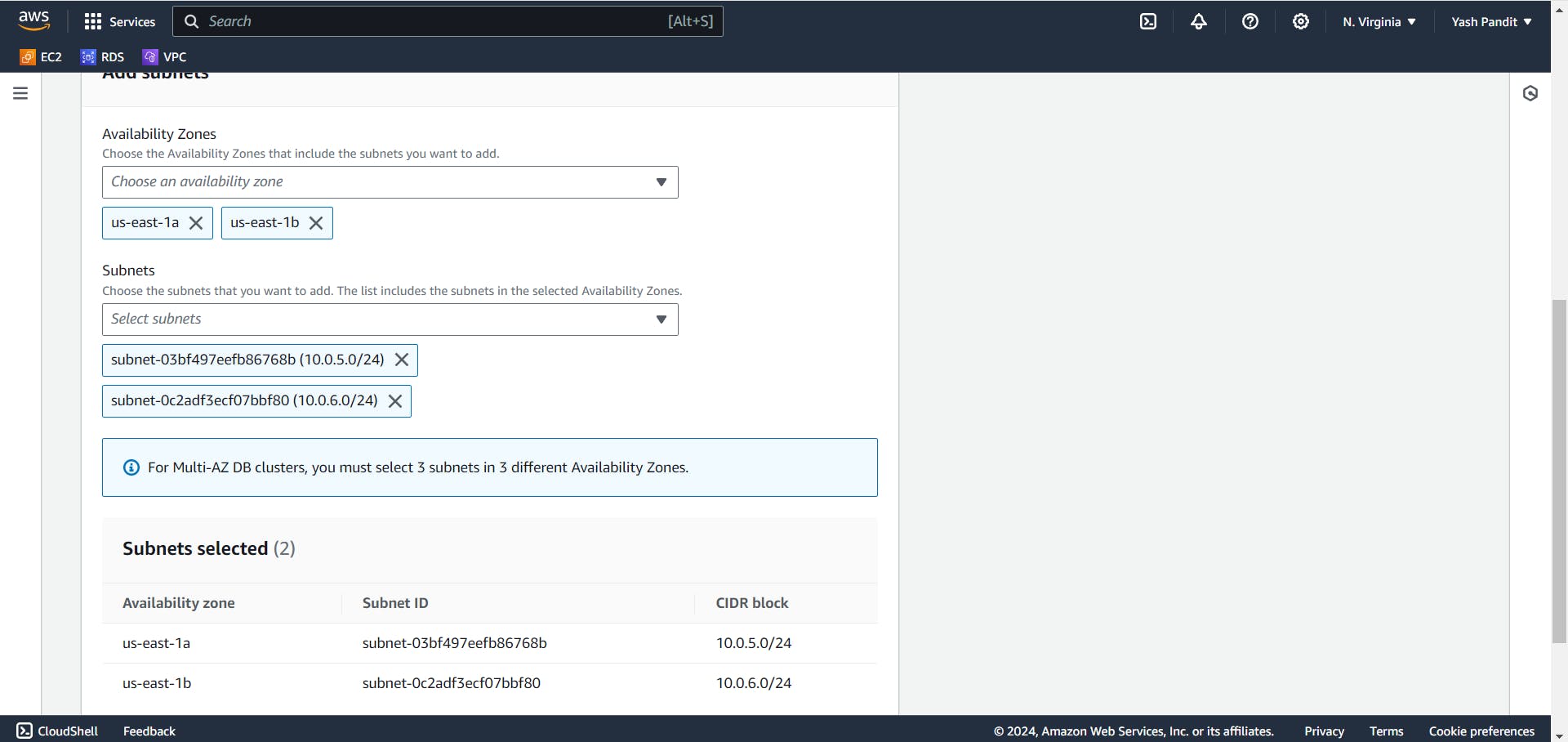
Include subnets from both availability zones:-
Availability Zone: - "us-east-1a", "us-east-1b"
Subnets - "10.0.5.0/24", "10.0.6.0/24"
Click on "Create"
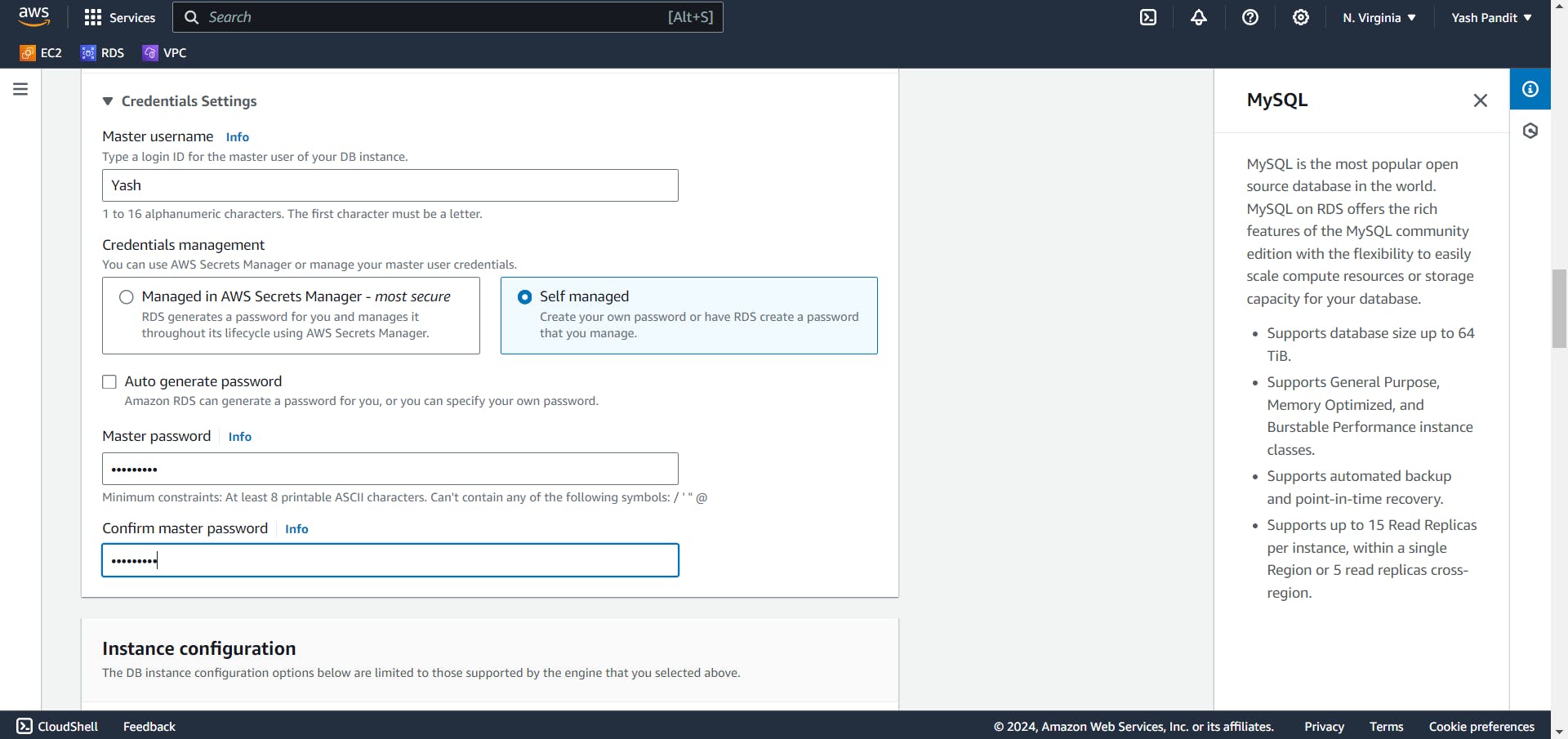
Creating a Database Instance (RDS):
Create a MySQL database instance named "database-1" with appropriate master username and appropriate password:-
Go to "Databases"
Click on "Create database"
Engine type - "MySQL"
If you want replication select "Production" or "Dev/Test" im going with "Free tier"
DB instance identifier - "database-1"
Give Master username and Master password as per your requirements.
Select DB instance class as per your requirements im using "db.t3.micro"
Set the DB subnet group to "three-tier-subnet-group":-
VPC - "vpc-for-3tier"
DB subnet group - "three-tier-subnet-group"
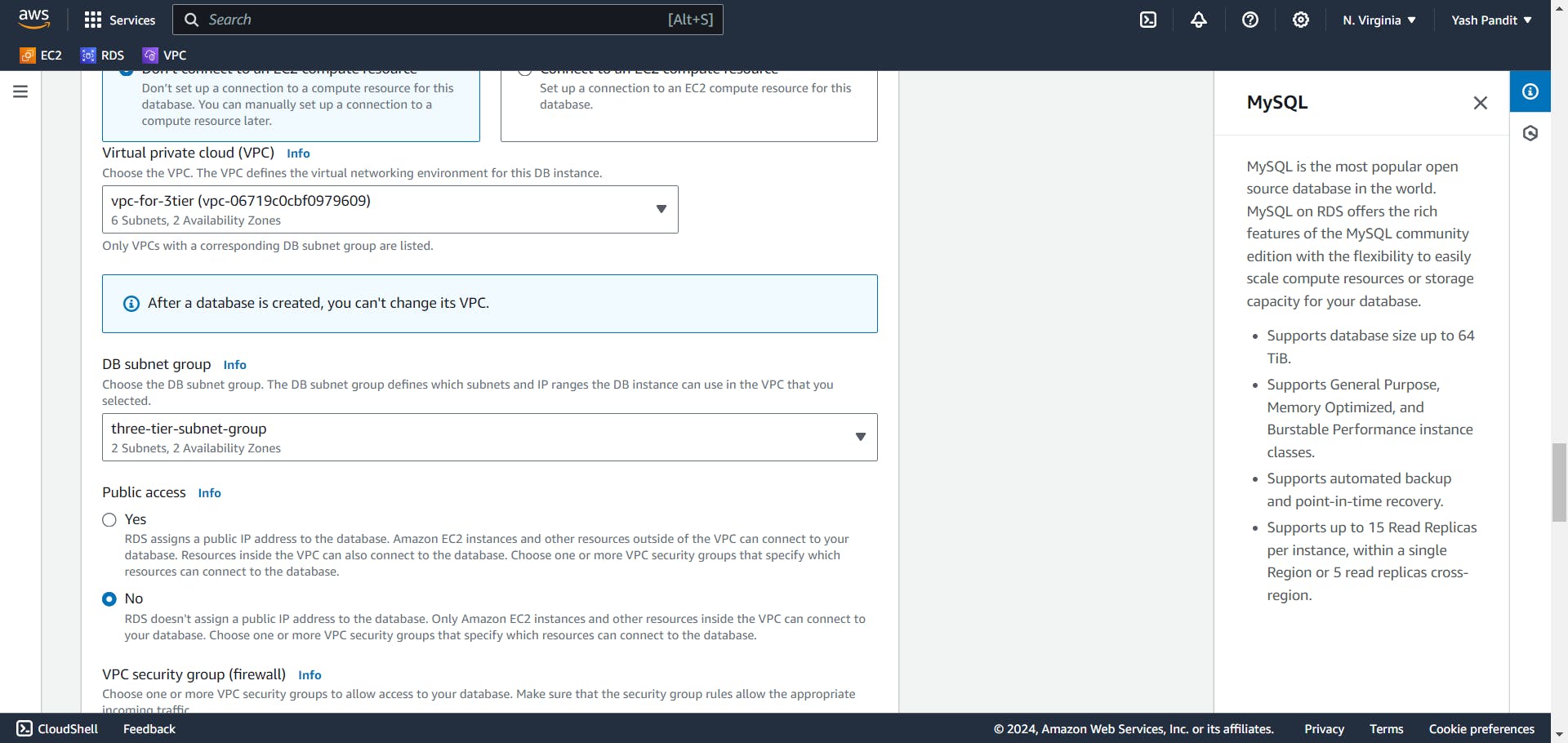
Restrict public access and assign the security group "DB-SG":-
Public access - "No"
VPC security group - "choose existing"
Existing VPC security groups - "DB-SG"
Availability Zone - "No preference"
Click on "Create database"
Step 4: Creating the Servers for frontend and backend Applications 💻
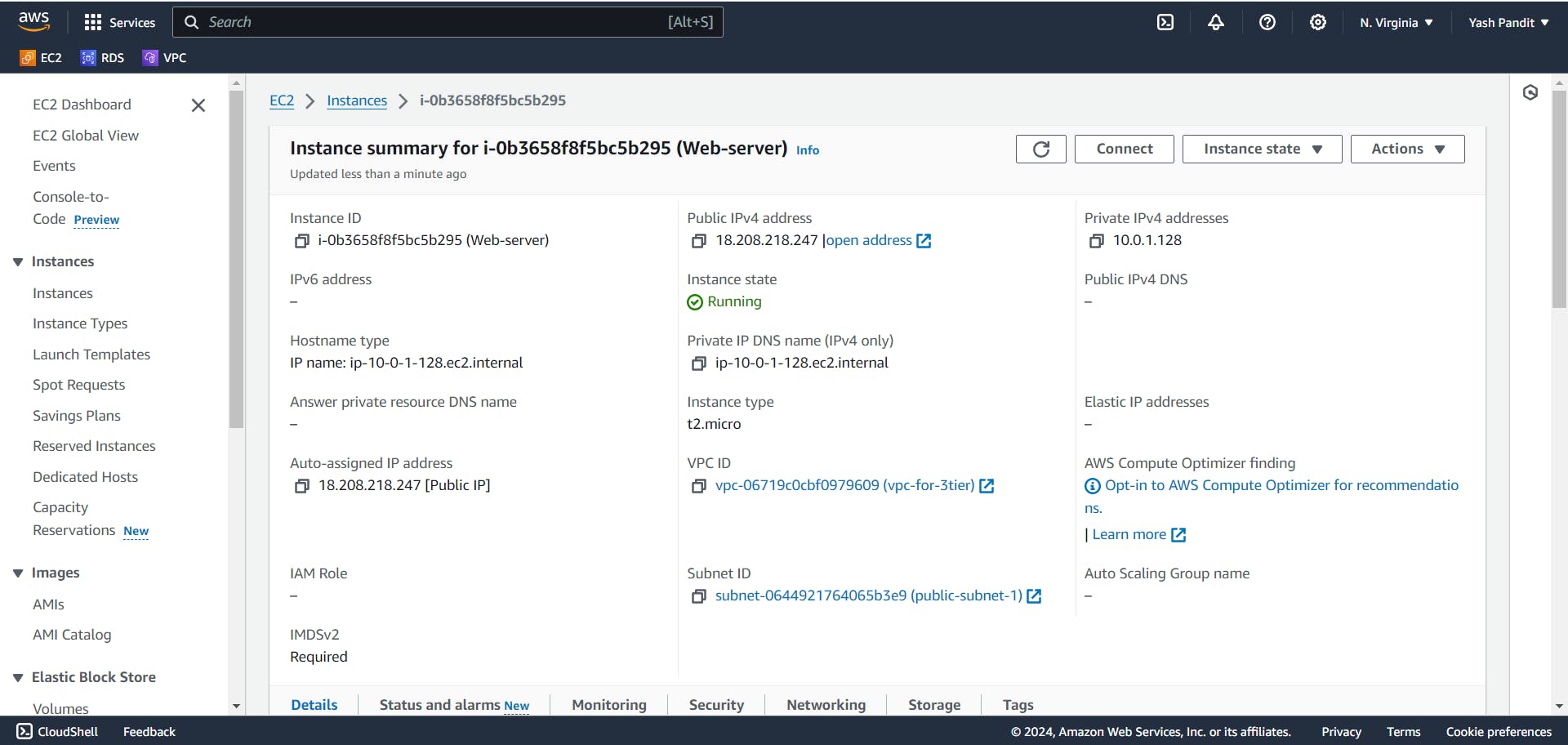
Launching EC2 Instances for frontend application:
Click on "Launch instances".
Name - "Web-server"
AMI - "Ubuntu"
Instance type - "t2.micro (free tier)"
Key pair : Create > "aws-project.pem" (Download the .pem file.)
VPC - "vpc-for-3tier"
Subnet - "public-subnet-1"
Auto-assign public IP - "Enable"
Firewall (security groups) - "Select existing security group"
security group - "Web-SG"
Click on "Launch instance"
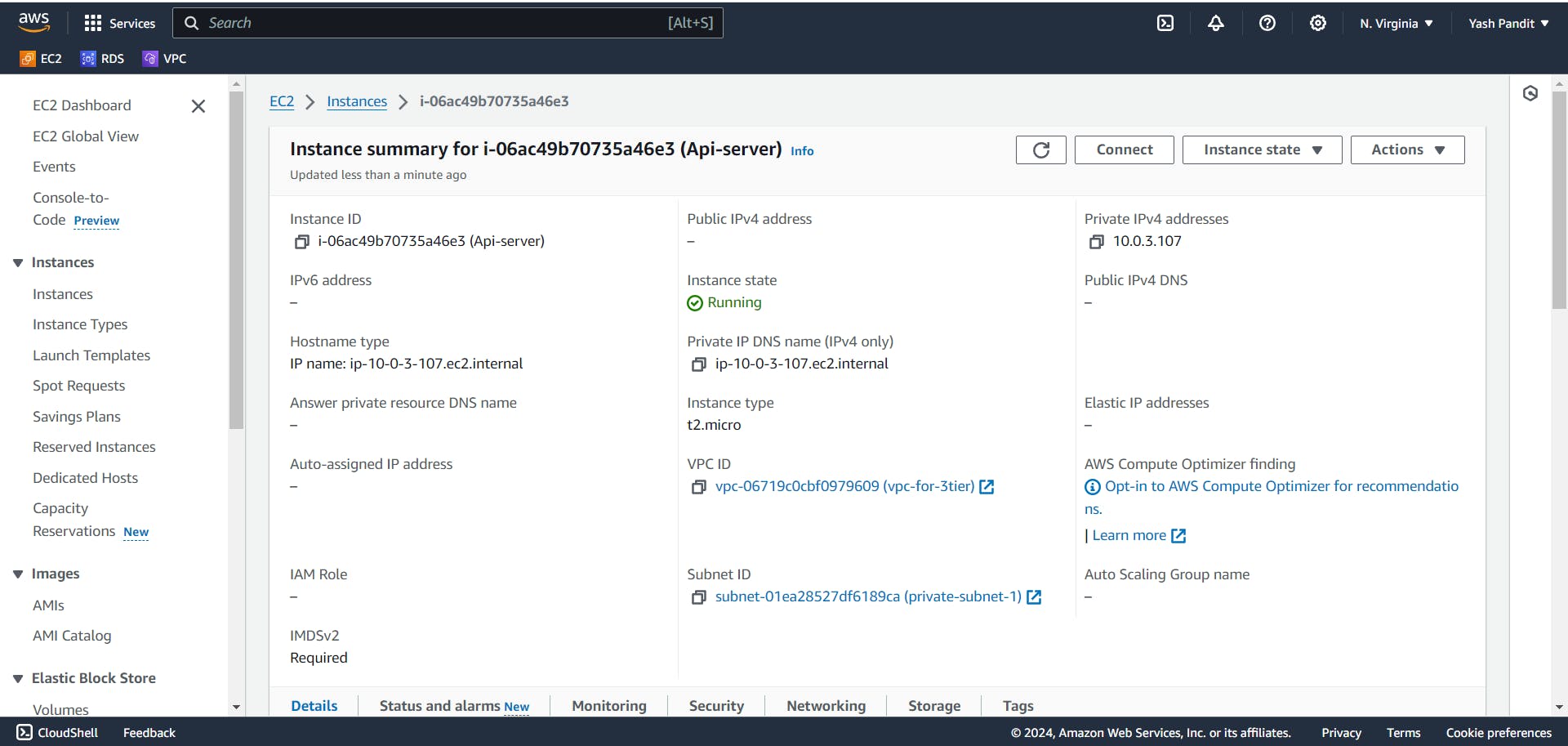
Launching EC2 Instances for backend application:
Click on "Launch instances".
Name - "Api-server"
AMI - "Ubuntu"
Instance type - "t2.micro (free tier)"
Key pair - "aws-project.pem"
VPC - "vpc-for-3tier"
Subnet - "private-subnet-1"
Auto-assign public IP - "Disable"
Firewall (security groups) - "Select existing security group"
security group - "Api-SG"
Click on "Launch instance"
Step 5: Setting up Database 🗃️
Connecting to Database Server:
Go to folder where your pem file is downloaded
SSH into the Frontend EC2 instance using the public IP address.(change pem key and public ip address as per your instance)
ssh -i 'aws-project.pem' ubuntu@18.208.218.247Now your in Web-server
copy pem key from your pc to web-server (Go to floder where your pem file is downloaded )
scp -i .\aws-project.pem -r .\aws-project.pem ubuntu@18.208.218.247:/home/ubuntu/change permision of your file(change file name)
sudo chmod 700 aws-project.pemSSH into the backend EC2 instance using the Private IP address.(change pem key and private ip address as per your instance)
ssh -i 'aws-project.pem' ubuntu@10.0.3.107Now your in Api-server
Update the server and install MySQL server.(It is important for acessing database)
sudo apt-get update sudo apt-get install mysql-server
Setting Up Database:
Go to AMAZON RDS and copy endpoint of your database
Connect to the RDS instance.(paste endpoint insted of host and change username as per you gave)
#copy your mysql database endpoint and put it instead of host #write your Master hostname instead of username mysql -h host -u username -pcreate a database named "employees".
Create necessary tables and configurations.
CREATE DATABASE employees; USE employees; CREATE TABLE employees ( id INT AUTO_INCREMENT PRIMARY KEY, name VARCHAR(255) NOT NULL, position VARCHAR(255) NOT NULL, salary DECIMAL(10, 2) NOT NULL ); INSERT INTO employees (name, position, salary) VALUES ('John Doe', 'Software Engineer', 75000.00), ('Jane Smith', 'Project Manager', 85000.00), ('Michael Johnson', 'Data Analyst', 65000.00);Now Exit from Mysql Database using exit command.
Step 6: Deploying the Backend Application 🐳
Setting Up backend:
Now, we are in Api-server.
Now, we are going to run our backend on docker container.
So, Install Docker on the EC2 instance.
sudo apt-get update sudo apt install docker.io sudo systemctl enable dockerClone the project from GitHub (https://github.com/yashrpandit/my-application-3tier.git).
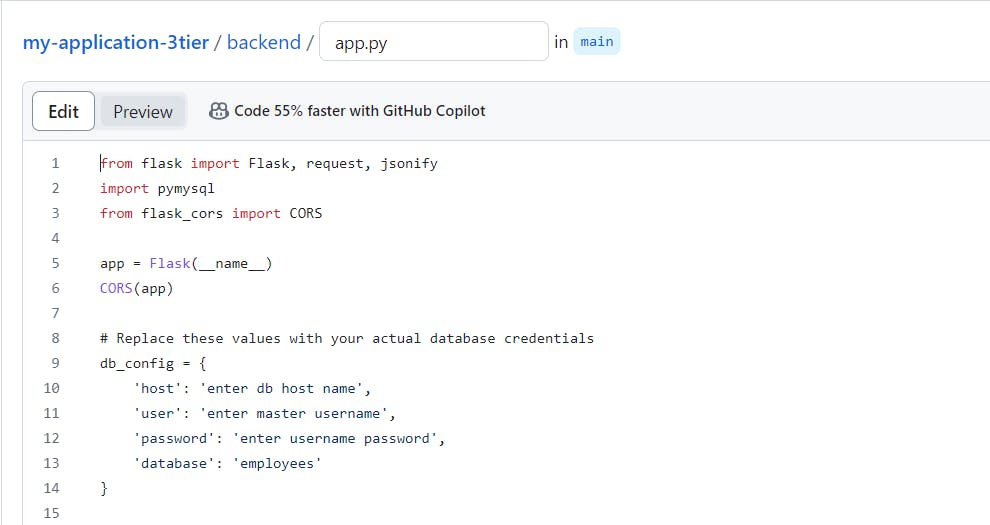
git clone https://github.com/yashrpandit/my-application-3tier.gitNavigate to the backend directory and edit app.py
cd my-application-3tier/backend/ sudo vi app.pychange the database credentials as per your database credentials.
build and run the backend application using docker on port 5000.
sudo docker build -t backendapp . sudo docker run -itd -p 5000:5000 --restart=always backendappExit from Api-server using exit command
Step 7: Setting Up Load Balancer and Auto Scaling For Backend application ⚖️
Creating AMI:
Select instance named "Api-server" and click on Actions>Image and templates>Create image.
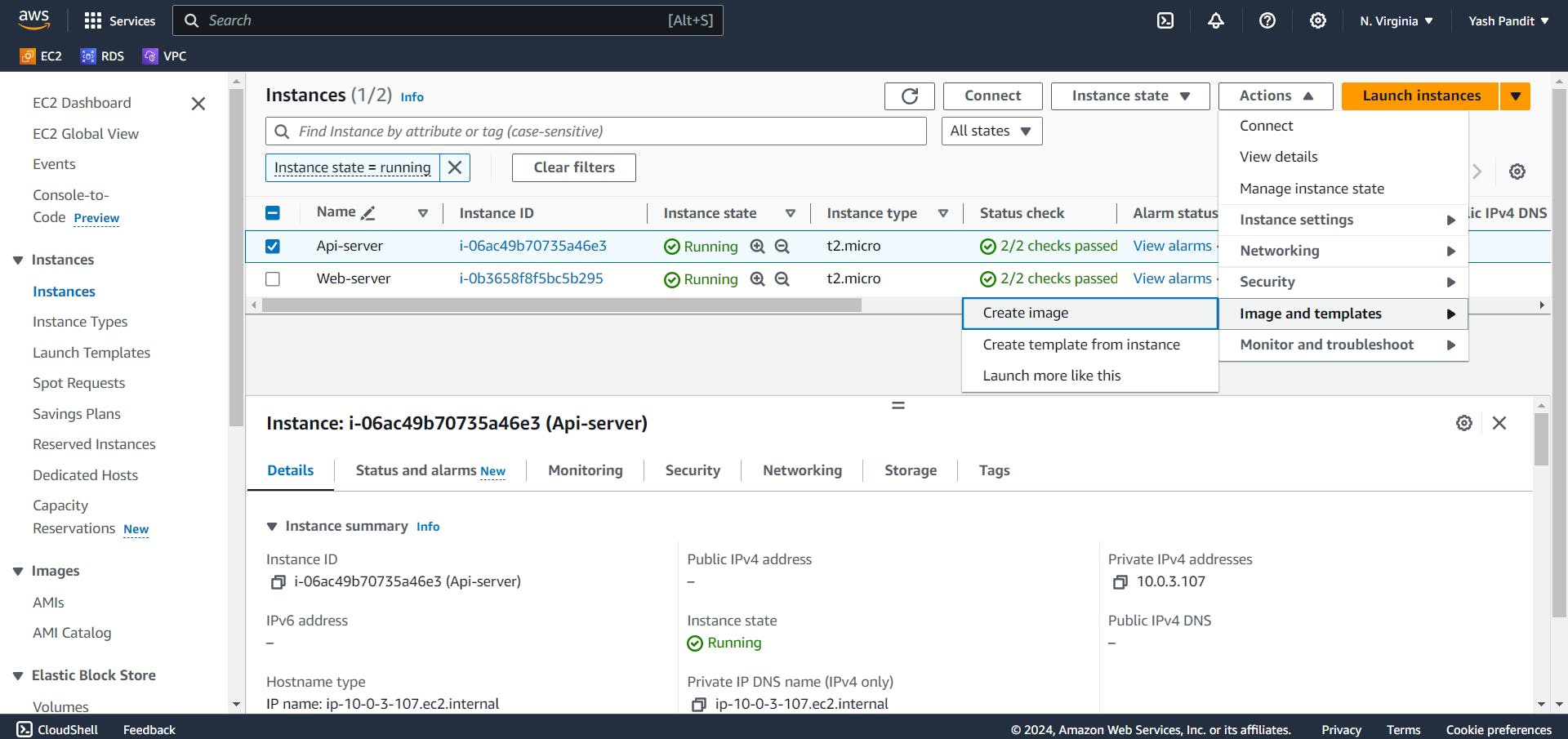
name - "Api-server-image"
Click on "Create image"
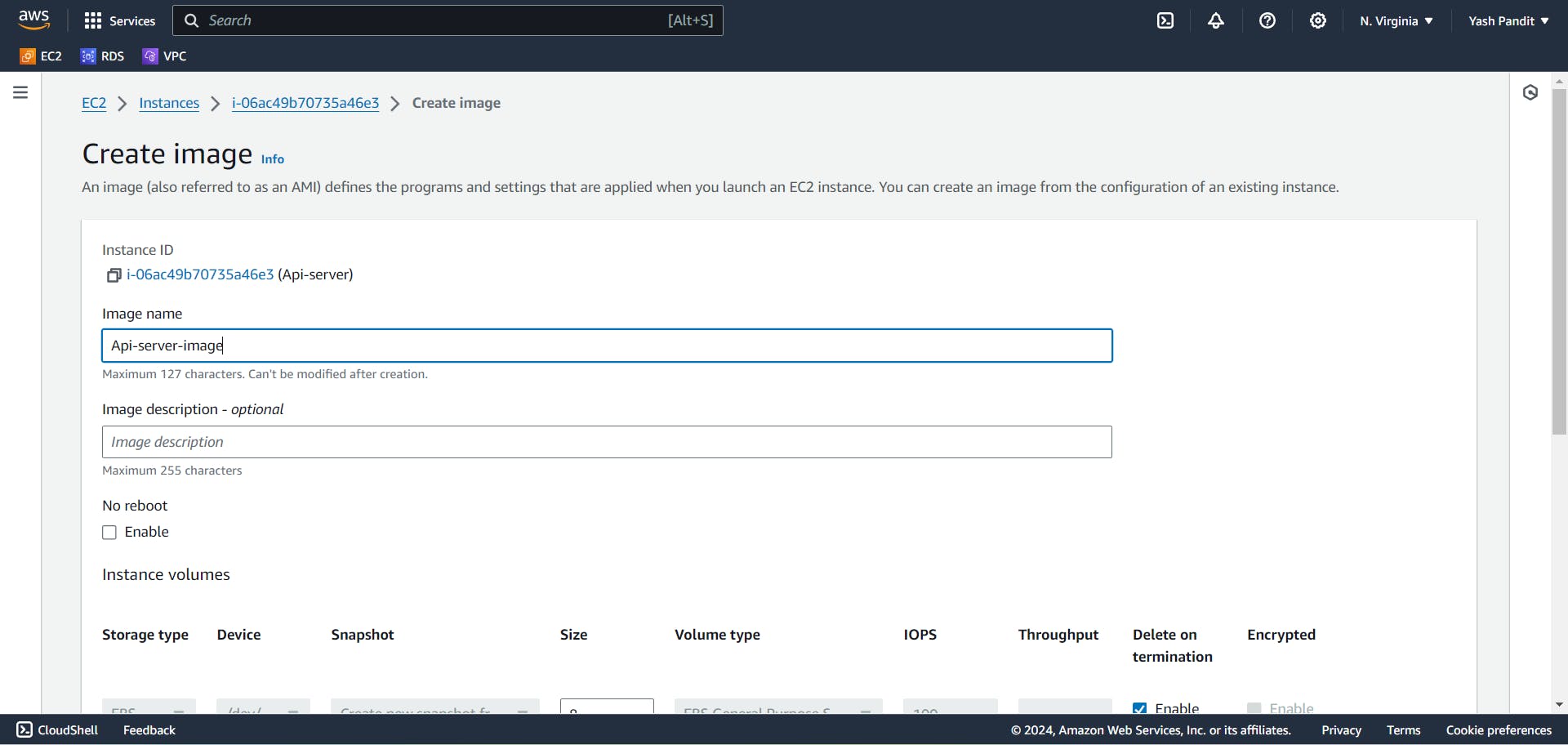
Creating Launch Template :
Go to Launch Template section under instances.
Click on "Create launch template"
Launch template name - "Api-server-launch-template"
select AMI named "Api-server-image" under My AMIs
instance type - "t2.micro"
key pair - "aws-project.pem"
Subnet - "Don't include in launch template"
Security group - "Api-SG"
Click on "Create launch template"
Creating Target Group:
Go to target group section under load balancing, Click on "Create target group".
target type - "instances"
target group name - "Api-TG" (for routing traffic to backend instances)
Protocol - "HTTP" , Port - "5000"
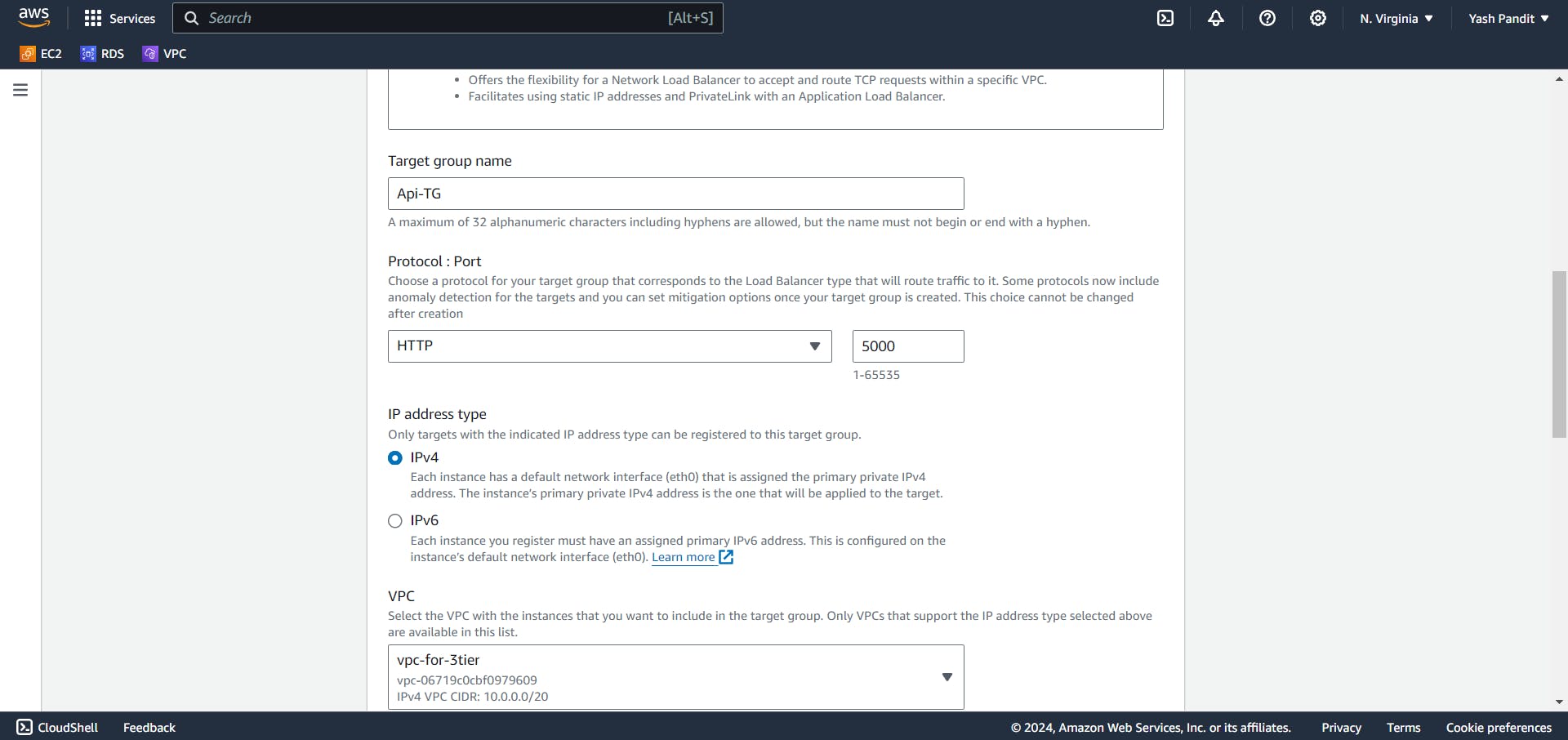
Select VPC - "vpc-for-3tier"
Protocol version - "HTTP1"
Set protocol to HTTP, health check protocol to HTTP, and health check path to "/".
Click on - "Next"
Don't choose any instance for target.
Click on "create target group"
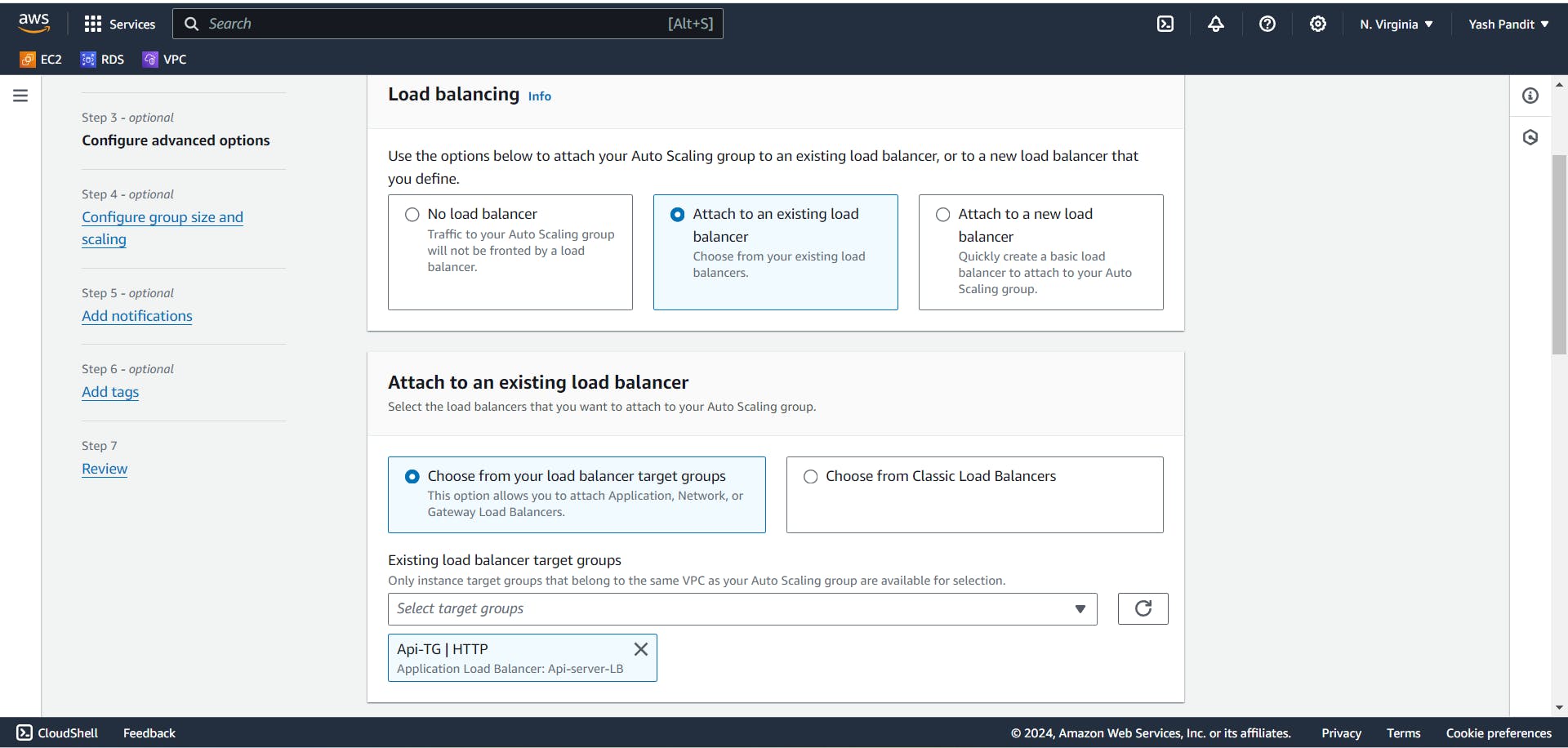
Creating Application Load Balancer (ALB):
Go to Load balancers section under Load balancing, Click on "Create load balancer" .
Select "Application load balancer" and Click on "Create"
Load balancer name - "Api-server-LB"
Scheme - "Internal"
IP address type - "IPv4"
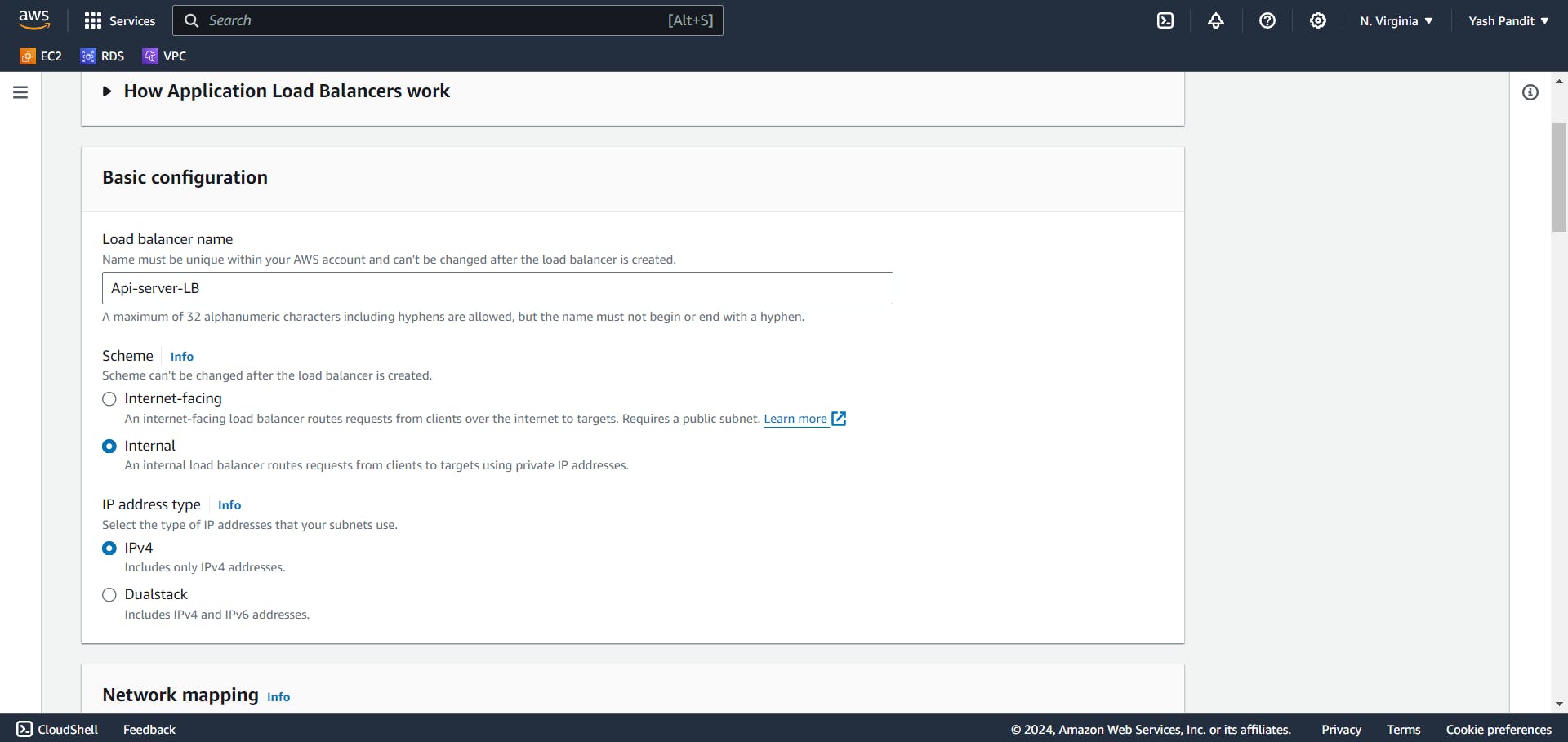
VPC - "vpc-for-3tier"
In Mappings select "us-east-1a" and "us-east-1b"
Select "private-subnet-1" under "us-east-1a" and "private-subnet-2" under "us-east-1b"
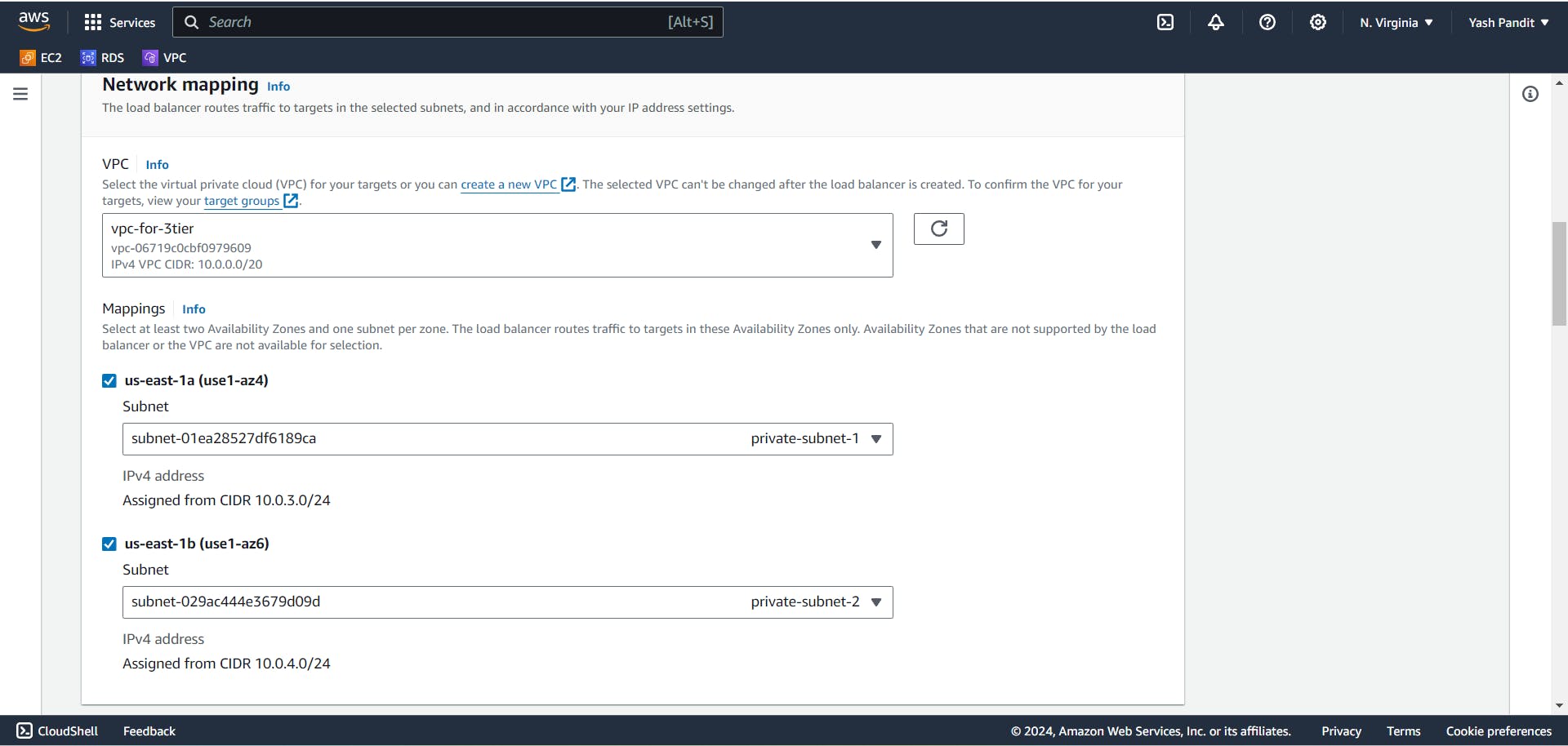
assign the security group - "Internal-LB".
Configure listener to forward HTTP traffic on port 80 to "Api-TG".
Click on "Create load balancer"
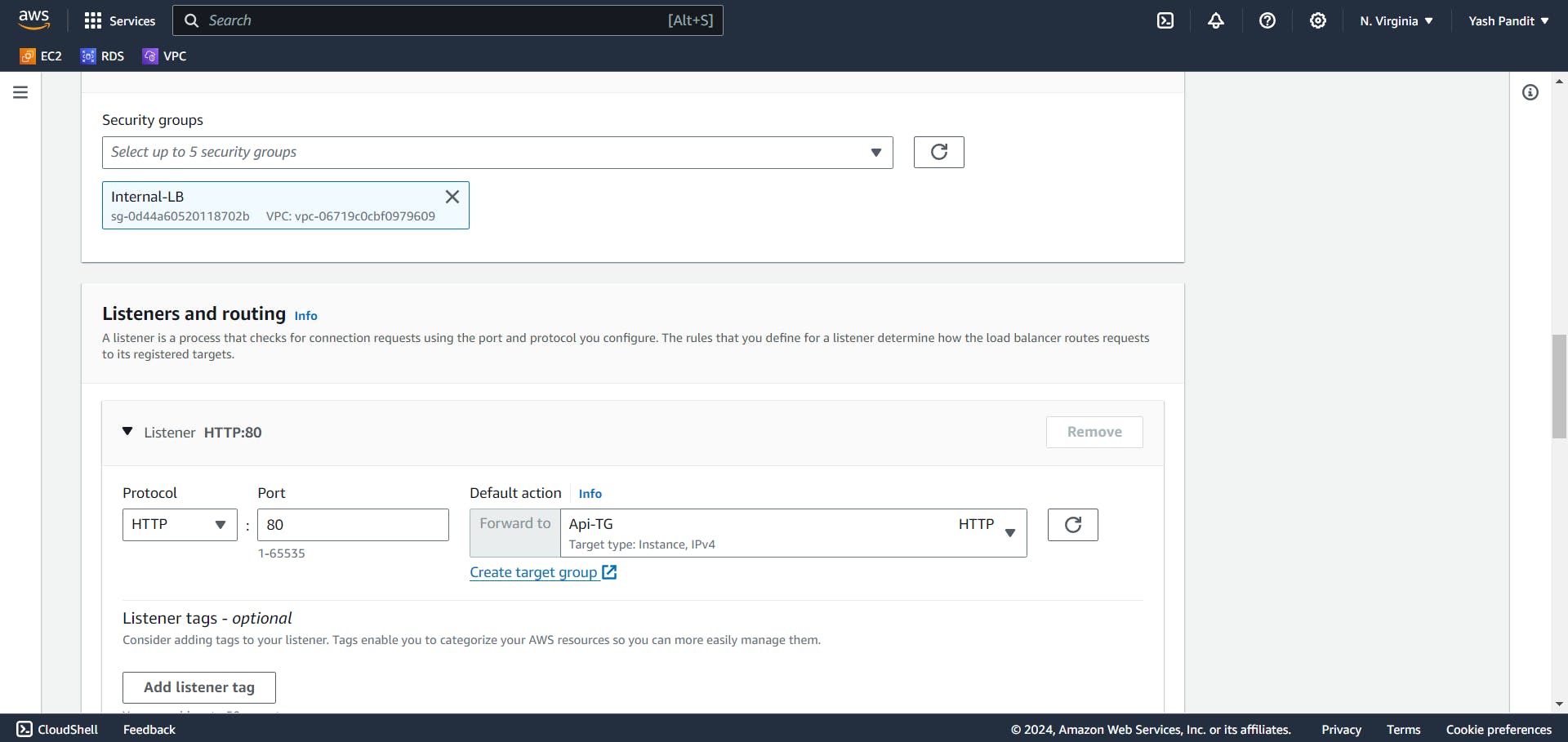
Creating Auto Scaling Group:
Go to Auto scaling groups section under Auto scaling.
Click on "Create Auto scaling group"
Auto Scaling group name - "scaling-api-server"
Launch template - "Api-server-launch-template"
click "next"
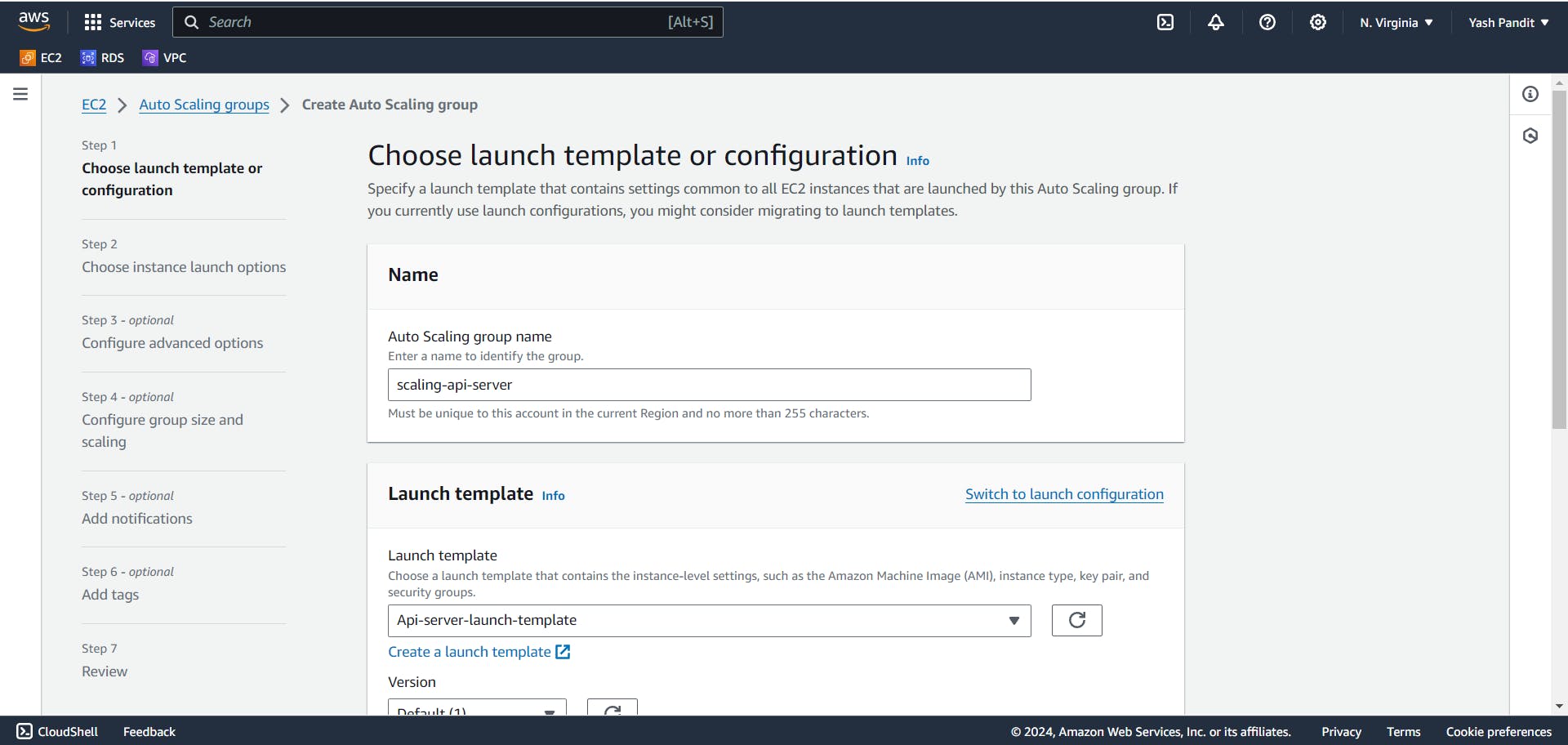
VPC - "vpc-for-3tier"
subnets - "private-subnet-1", "private-subnet-2"
Click on "Next"
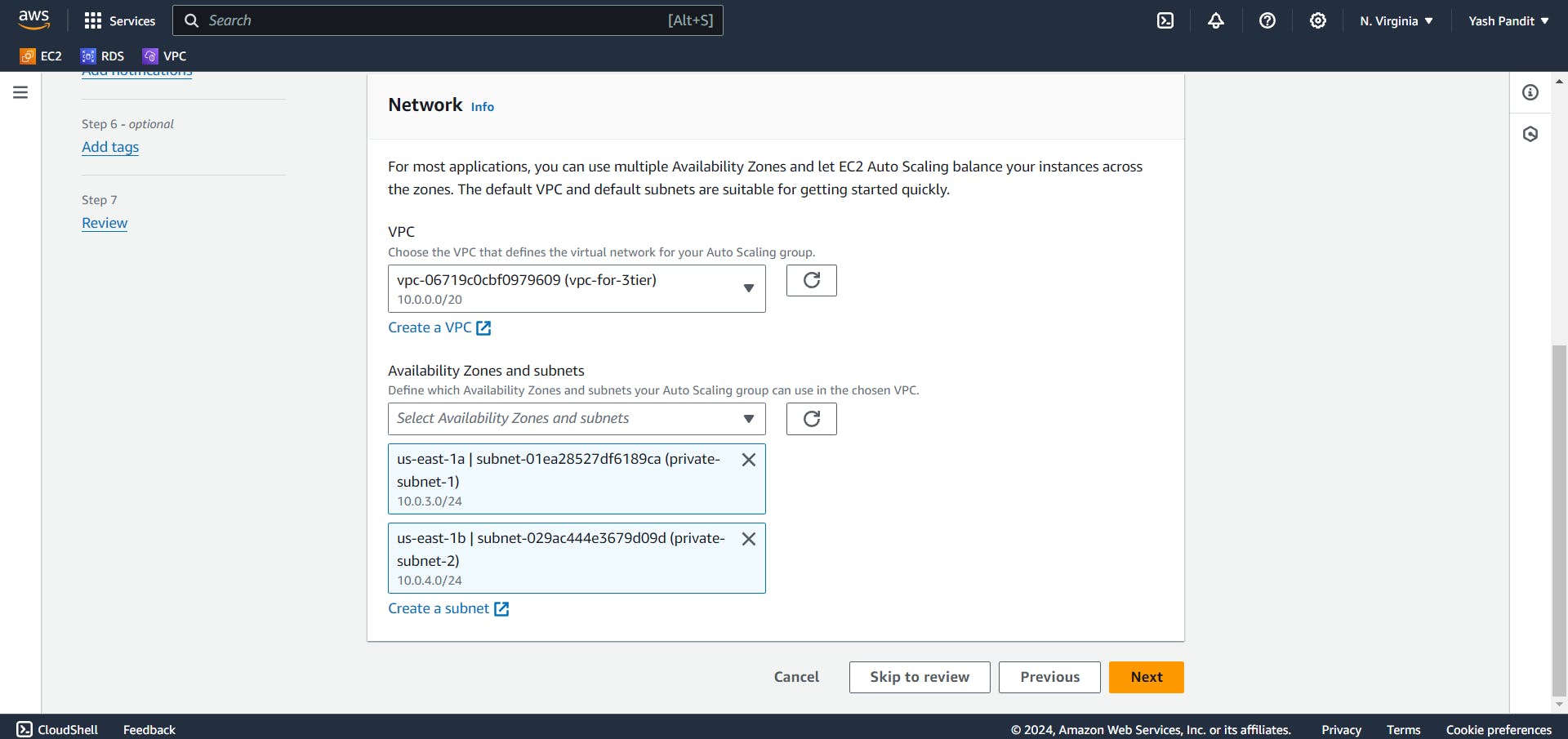
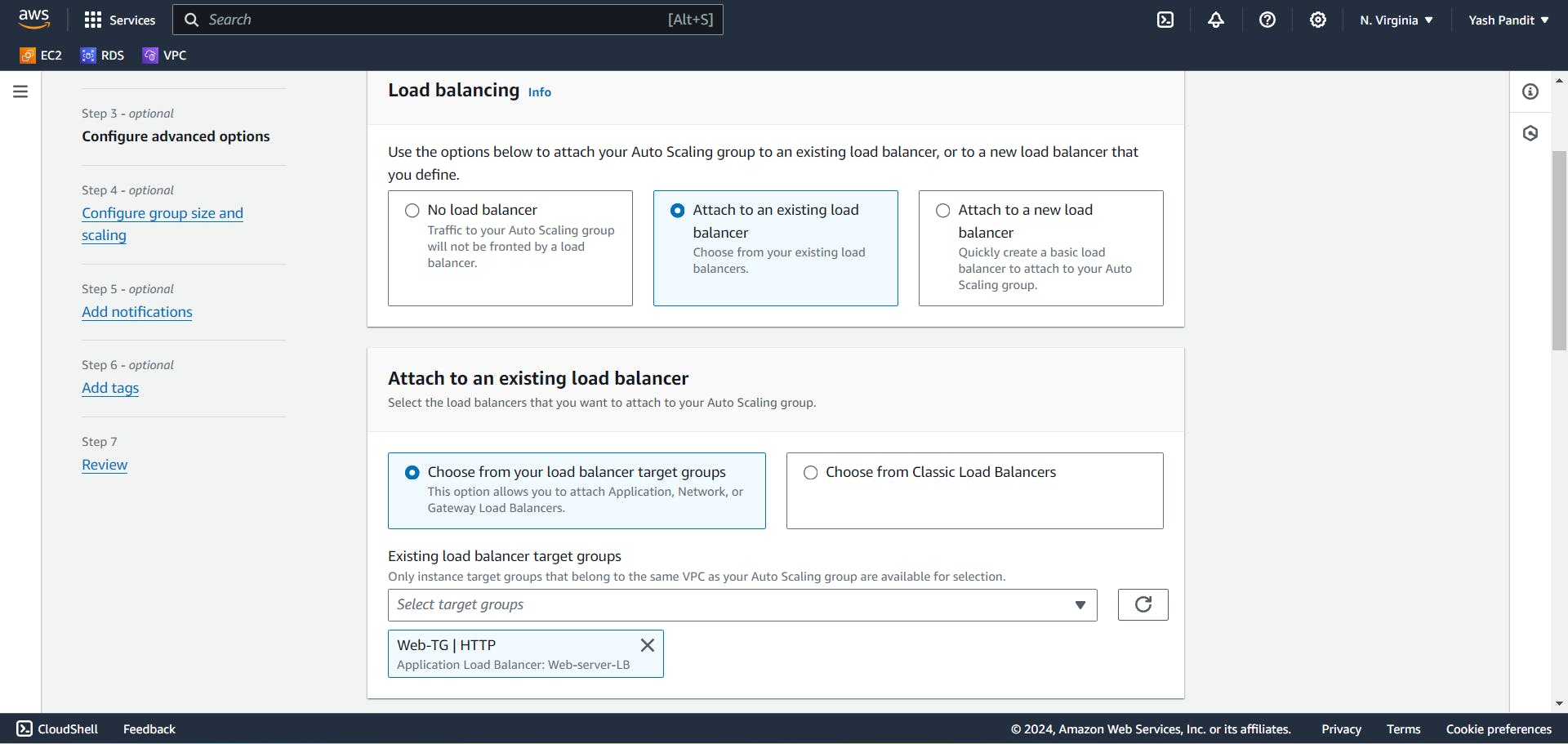
Select "Attach to an existing load balancer" and select target group "Api-TG".
click on "Next"
Configure scaling policies with desired, minimum, and maximum capacity as per your requirements
I select desired capacity "2", Min desired capacity "2", Max desired capacity "2"
Click on "Next"
Set notifications and tag if you want
Click on "Next"
Review it and click on "Create"
Step 8: Deploying the Frontend Application 🐳
Connecting to Web-Server:
If your not in the Web-server then Go to folder where your pem file is downloaded
SSH into the Frontend EC2 instance using the public IP address.(change pem key and public ip address as per your instance)
ssh -i 'aws-project.pem' ubuntu@18.208.218.247Now, we are in Web-server.
Setting Up Frontend :
Now, we are going to run our Frontend on docker container.
So, Install Nginx and Docker on the EC2 instance.
sudo apt-get update sudo apt install nginx sudo apt install docker.io sudo systemctl enable nginx sudo systemctl enable dockerClone the project from GitHub (https://github.com/yashrpandit/my-application-3tier.git).
git clone https://github.com/yashrpandit/my-application-3tier.gitNavigate to the frontend directory.
cd cd my-application-3tier/frontendbuild the app and run it on port 81.
sudo docker build -t webapp . sudo docker run -itd -p 81:80 --restart=always webapp
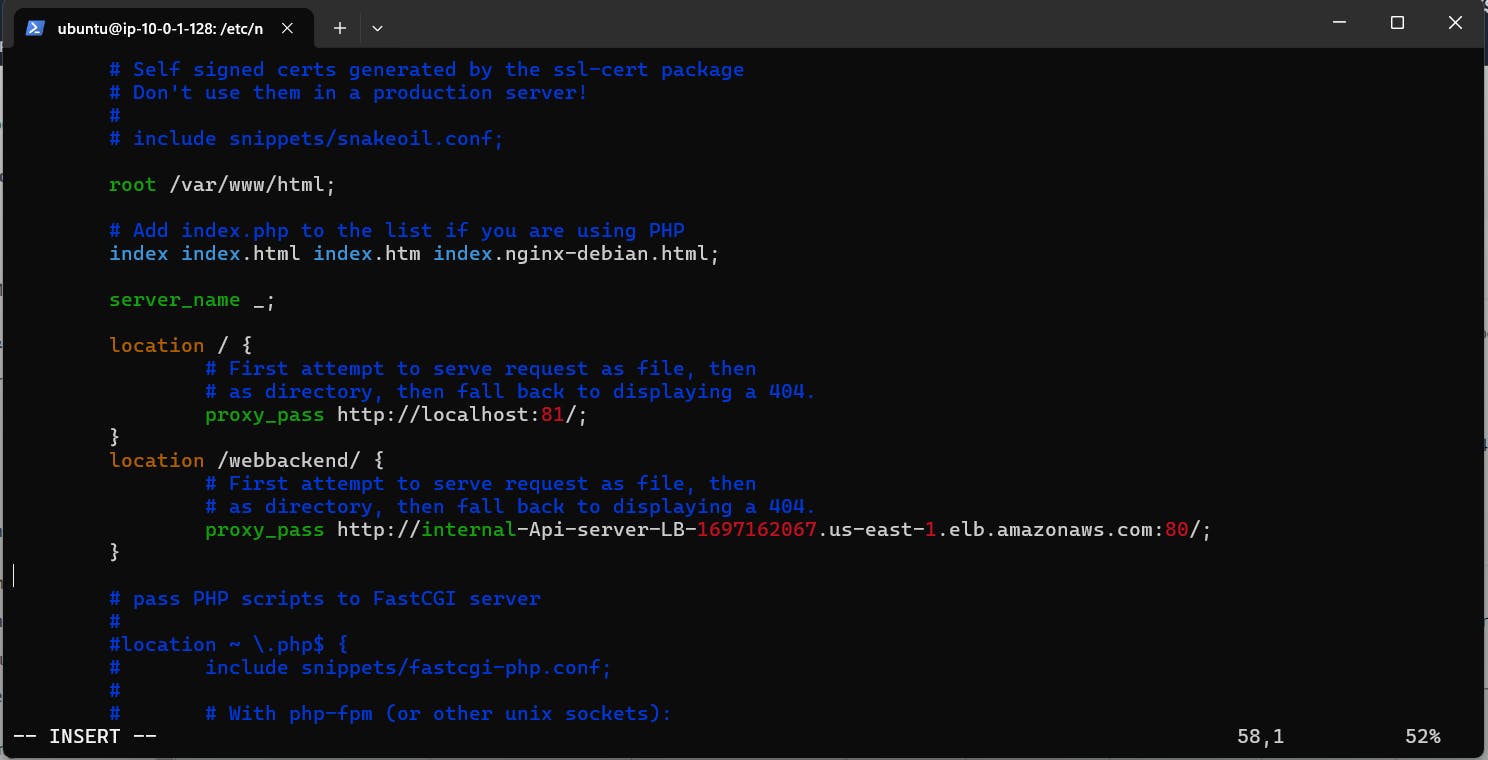
Configuring Nginx:
Edit the Nginx configuration file (/etc/nginx/sites-enabled/default)
proxy pass requests / to localhost:81 and /webbackend/ to internal-loadbalancer-dns:80
Step 9: Setting Up Load Balancer and Auto Scaling For Frontend application ⚖️
Creating AMI:
Select instance named "Web-server" and click on Actions>Image and templates>Create image.
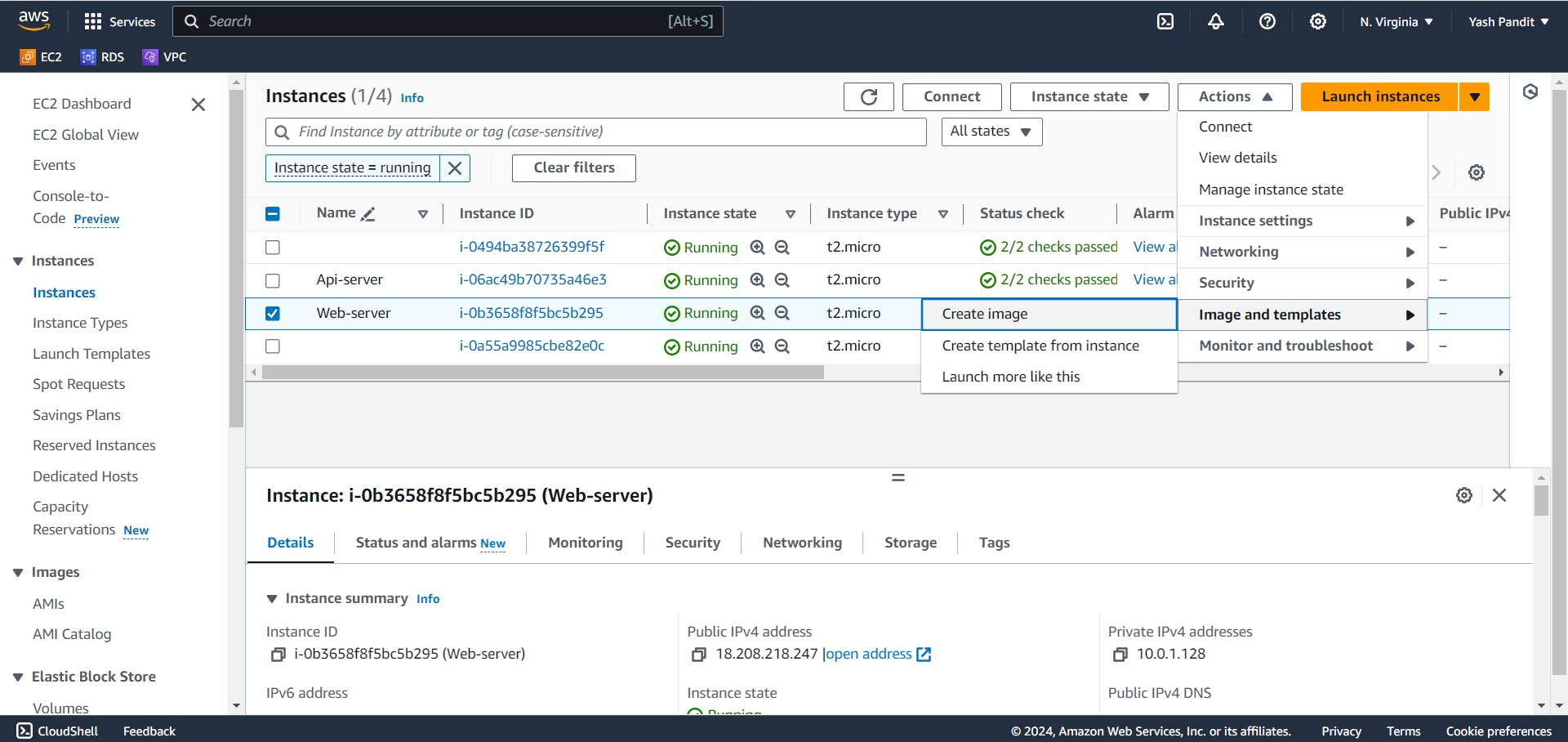
name - "Web-server-image"
Click on "Create image"
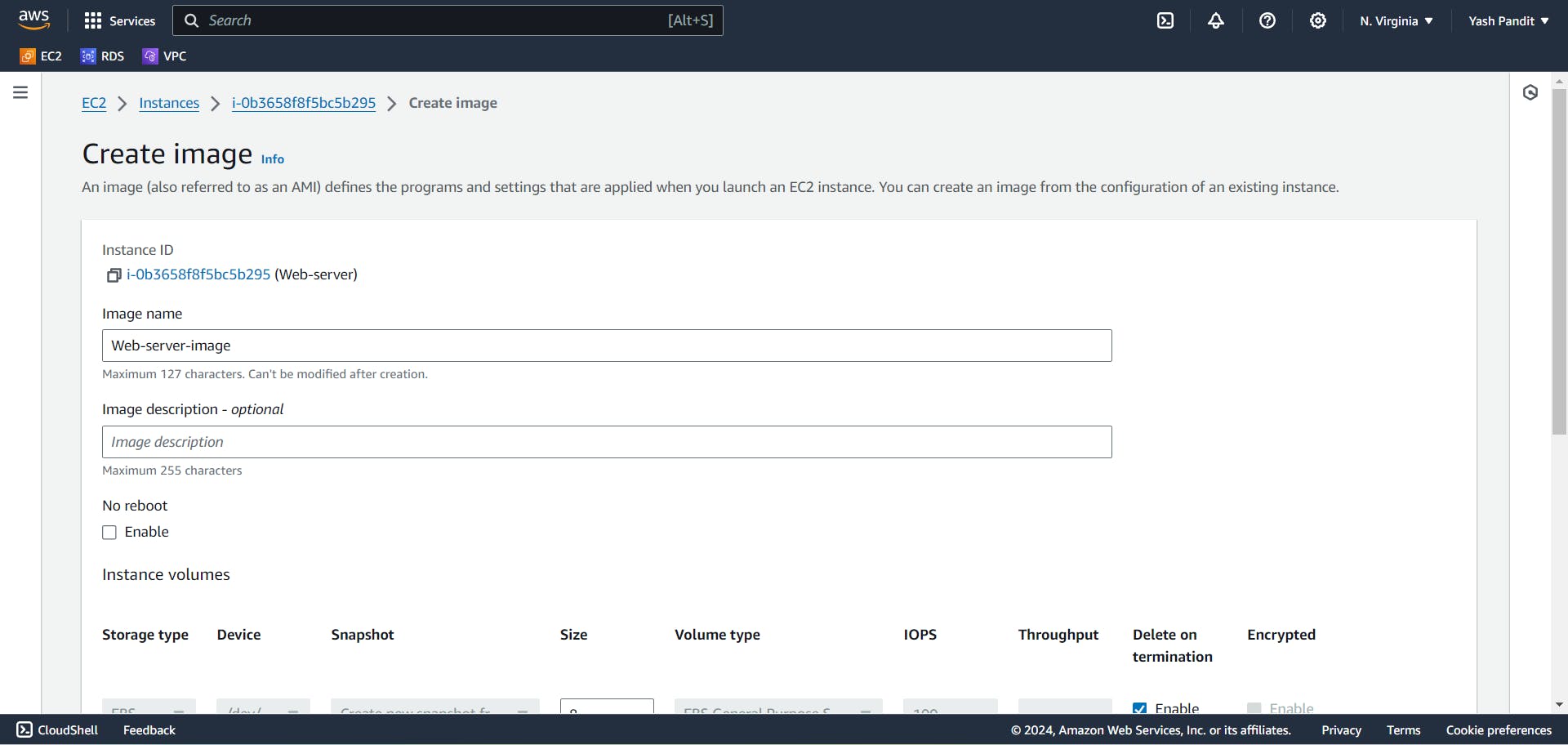
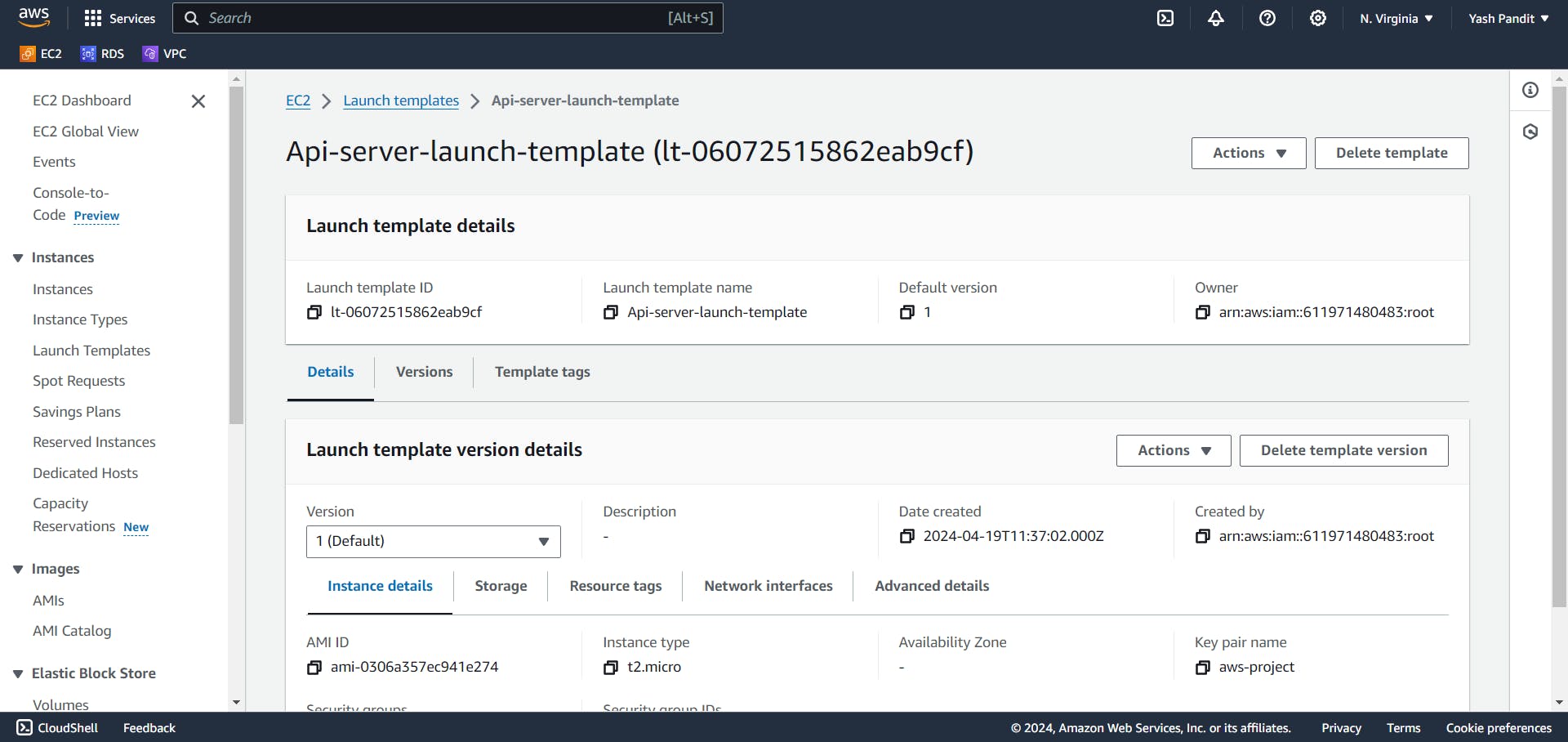
Creating Launch Template :
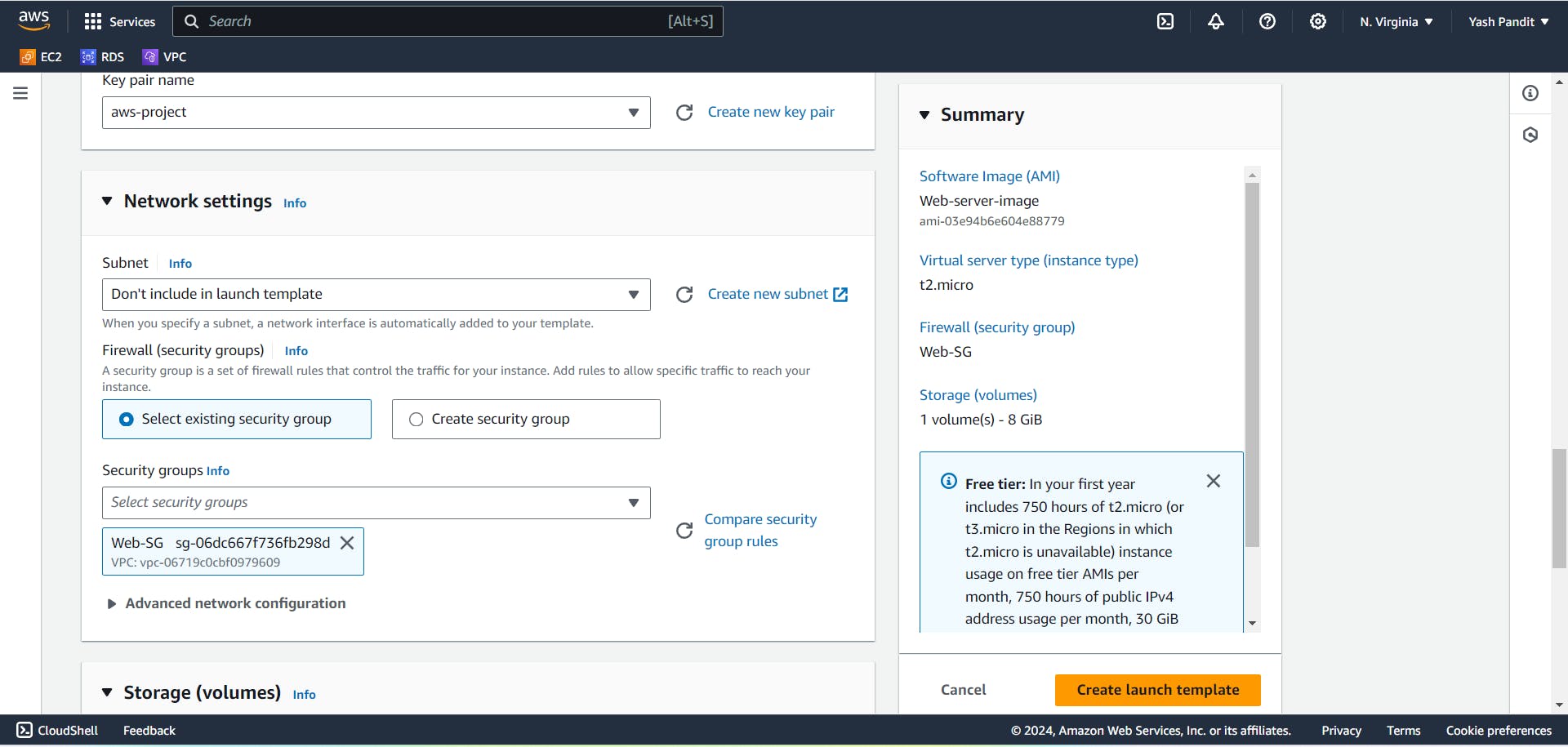
Go to Launch Template section under instances.
Click on "Create launch template"
Launch template name - "Web-server-launch-template"
select AMI named "Web-server-image" under My AMIs
instance type - "t2.micro"
key pair - "aws-project.pem"
Subnet - "Don't include in launch template"
Security group - "Web-SG"
Click on "Create launch template"
Creating Target Group:
Go to target group section under load balancing, Click on "Create target group".
target type - "instances"
target group name - "Web-TG" (for routing traffic to backend instances)
Protocol - "HTTP" , Port - "80"
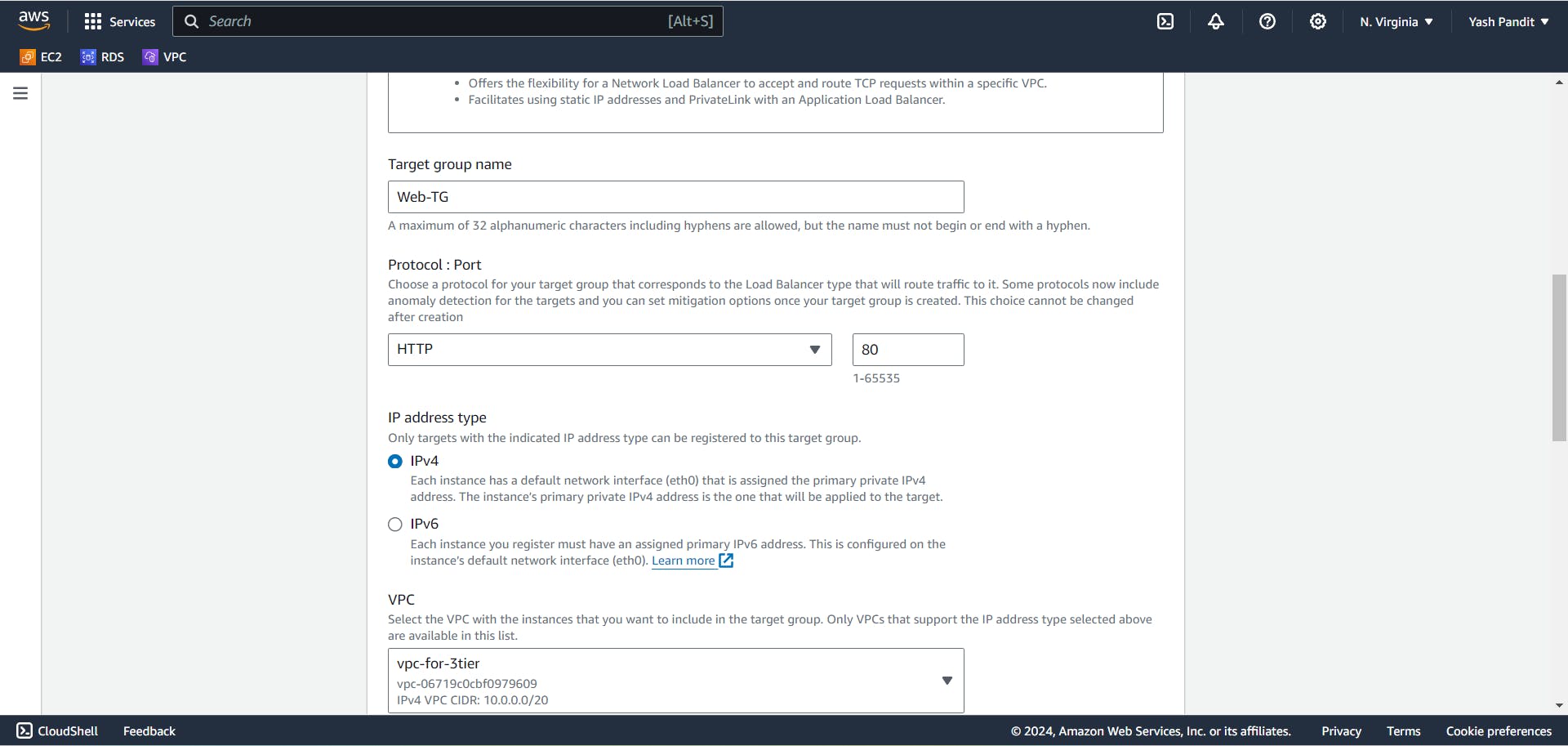
Select VPC - "vpc-for-3tier"
Protocol version - "HTTP1"
Set protocol to HTTP, health check protocol to HTTP, and health check path to "/".
Click on - "Next"
Don't choose any instance for target.
Click on "create target group"
Creating Application Load Balancer (ALB):
Go to Load balancers section under Load balancing, Click on "Create load balancer" .
Select "Application load balancer" and Click on "Create"
Load balancer name - "Web-server-LB"
Scheme - "Internet-facing"
IP address type - "IPv4"
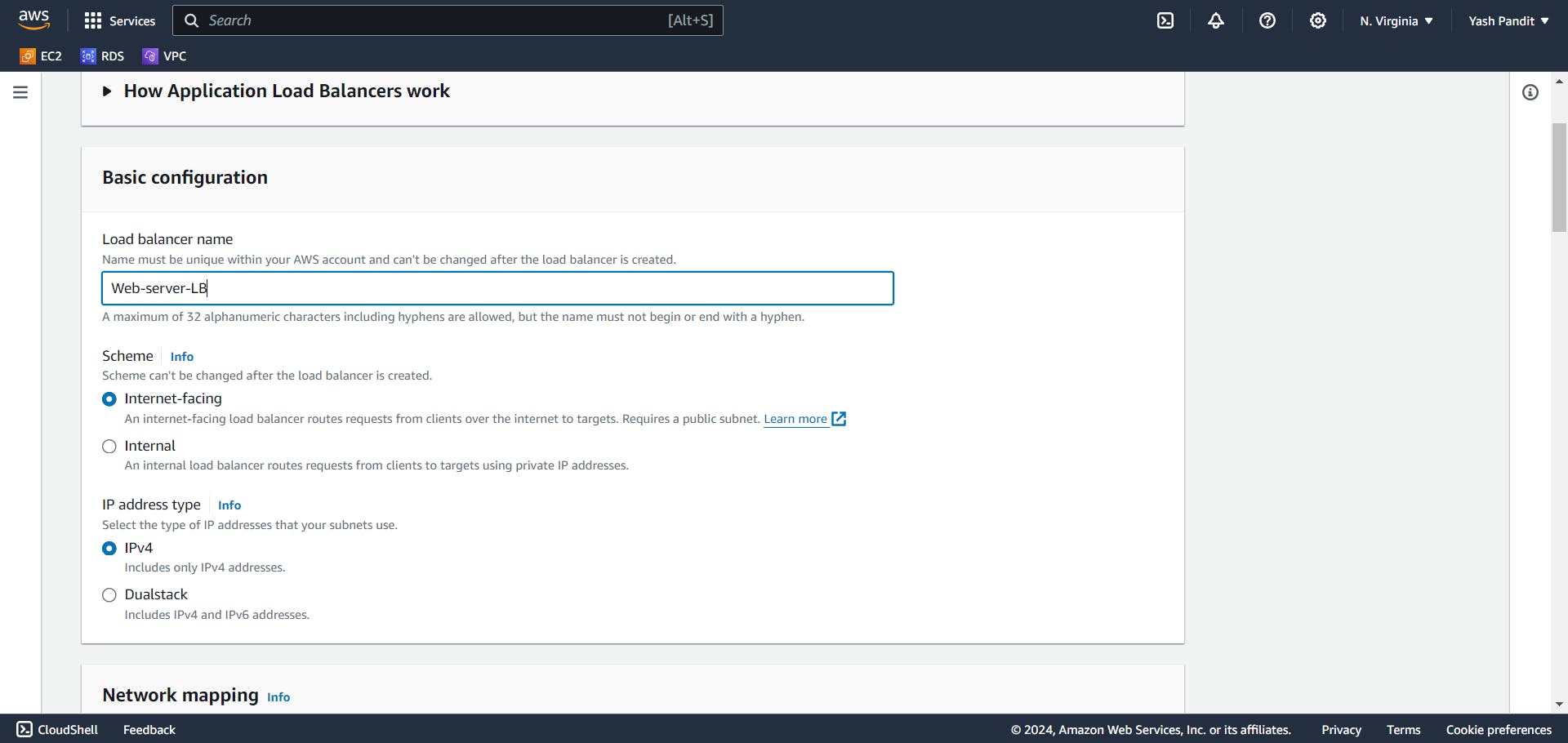
VPC - "vpc-for-3tier"
In Mappings select "us-east-1a" and "us-east-1b"
Select "public-subnet-1" under "us-east-1a" and "public-subnet-2" under "us-east-1b"
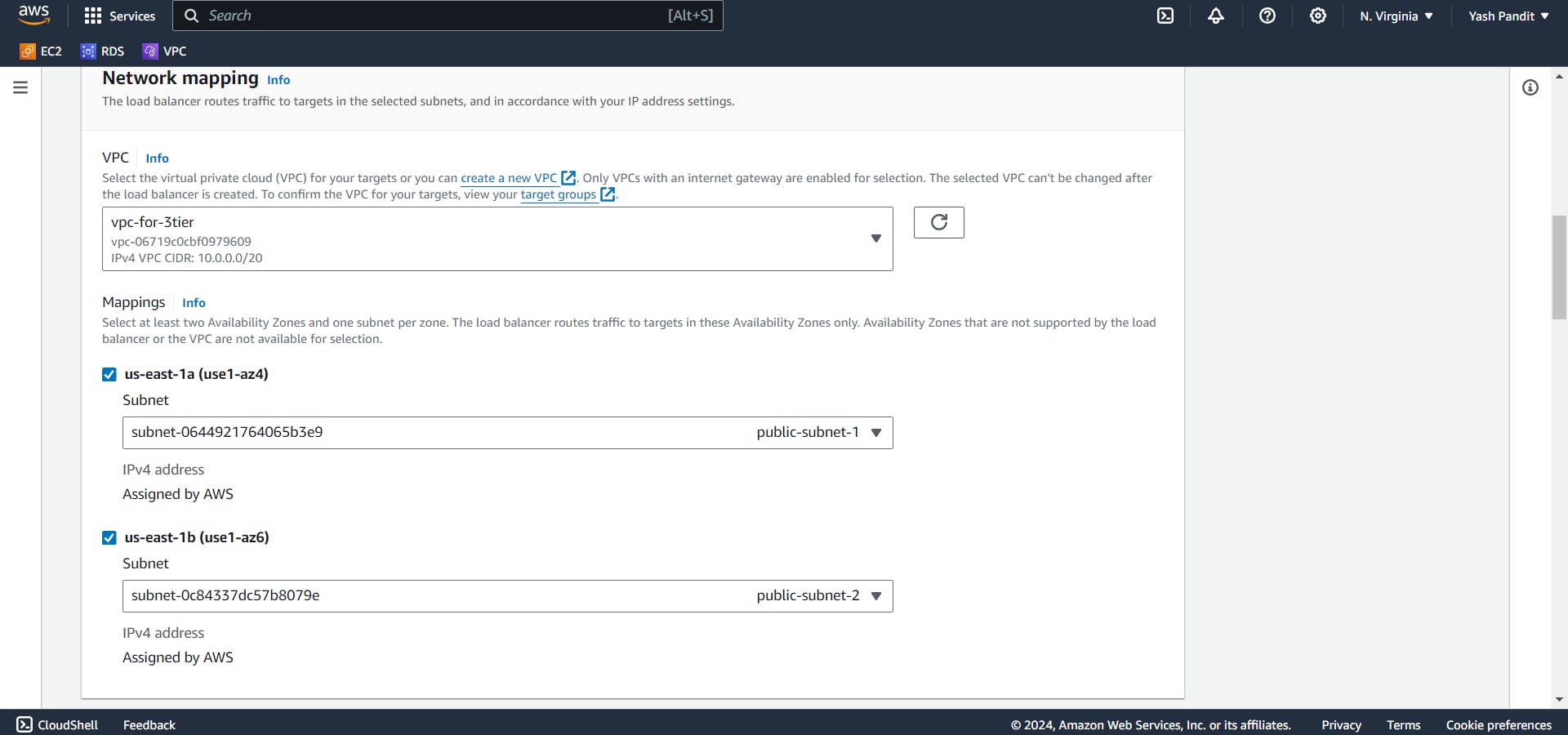
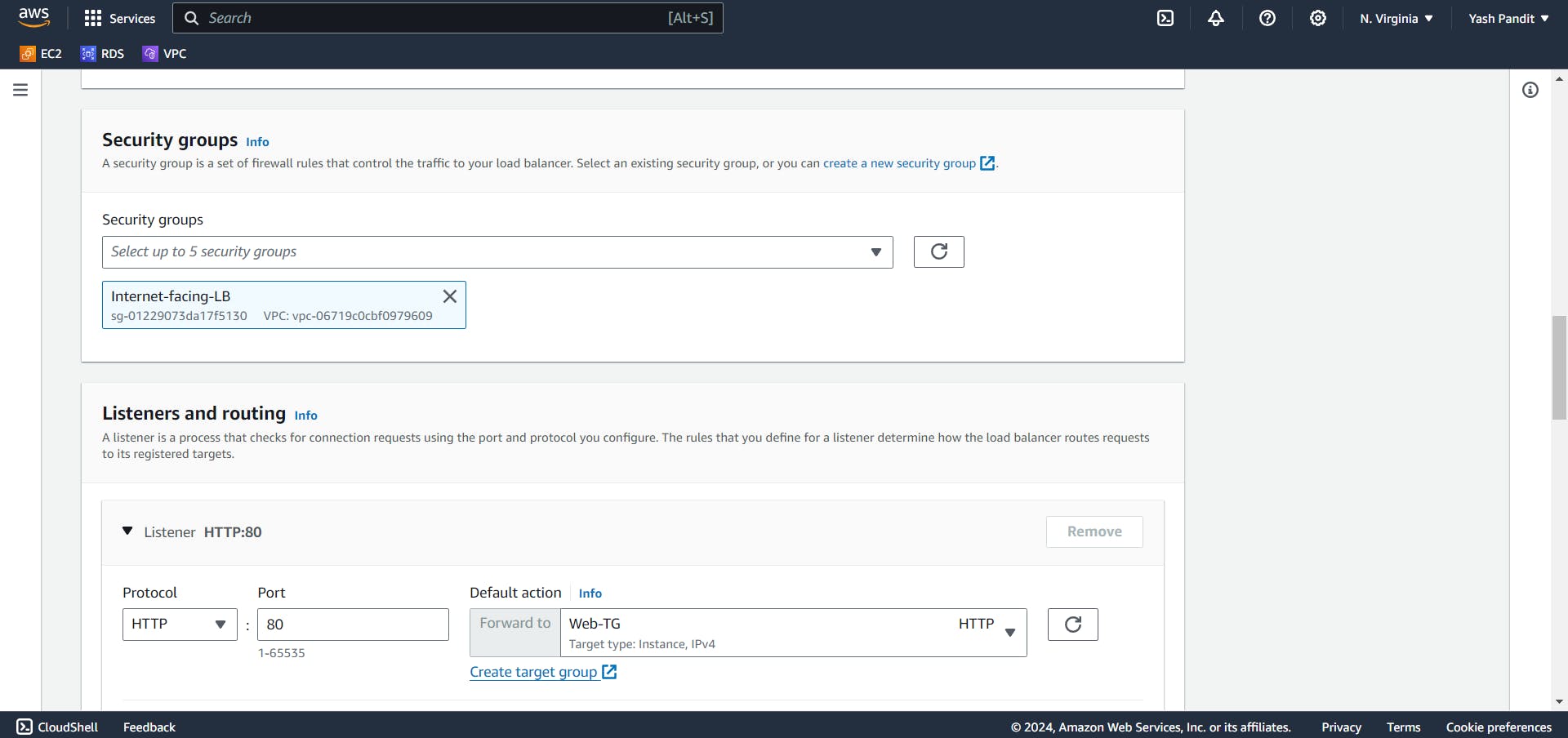
assign the security group - "Internet-facing-LB".
Configure listener to forward HTTP traffic on port 80 to "Web-TG".
Click on "Create load balancer"
Creating Auto Scaling Group:
Go to Auto scaling groups section under Auto scaling.
Click on "Create Auto scaling group"
Auto Scaling group name - "scaling-web-server"
Launch template - "Web-server-launch-template"
click "next"
VPC - "vpc-for-3tier"
subnets - "public-subnet-1", "public-subnet-2"
Click on "Next"
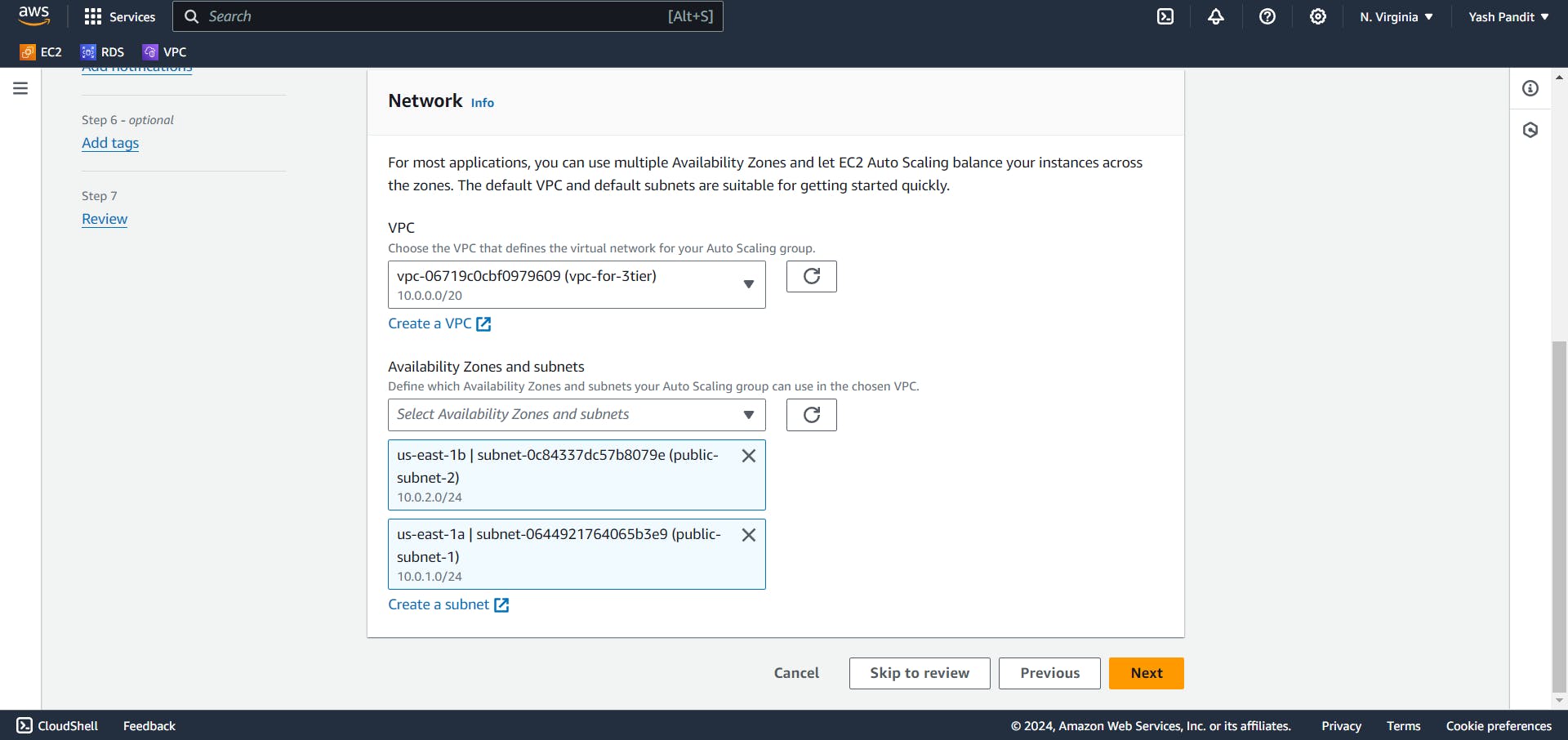
Select "Attach to an existing load balancer" and select target group "Web-TG".
click on "Next"
Configure scaling policies with desired, minimum, and maximum capacity as per your requirements
I select desired capacity "2", Min desired capacity "2", Max desired capacity "2"
Click on "Next"
Set notifications and tag if you want
Click on "Next"
Review it and click on "Create"
Step 10: Accessing the Application 🌐
Accessing the Application:
Copy the DNS name of the ALB ("Web-server-LB") and access the application through it.
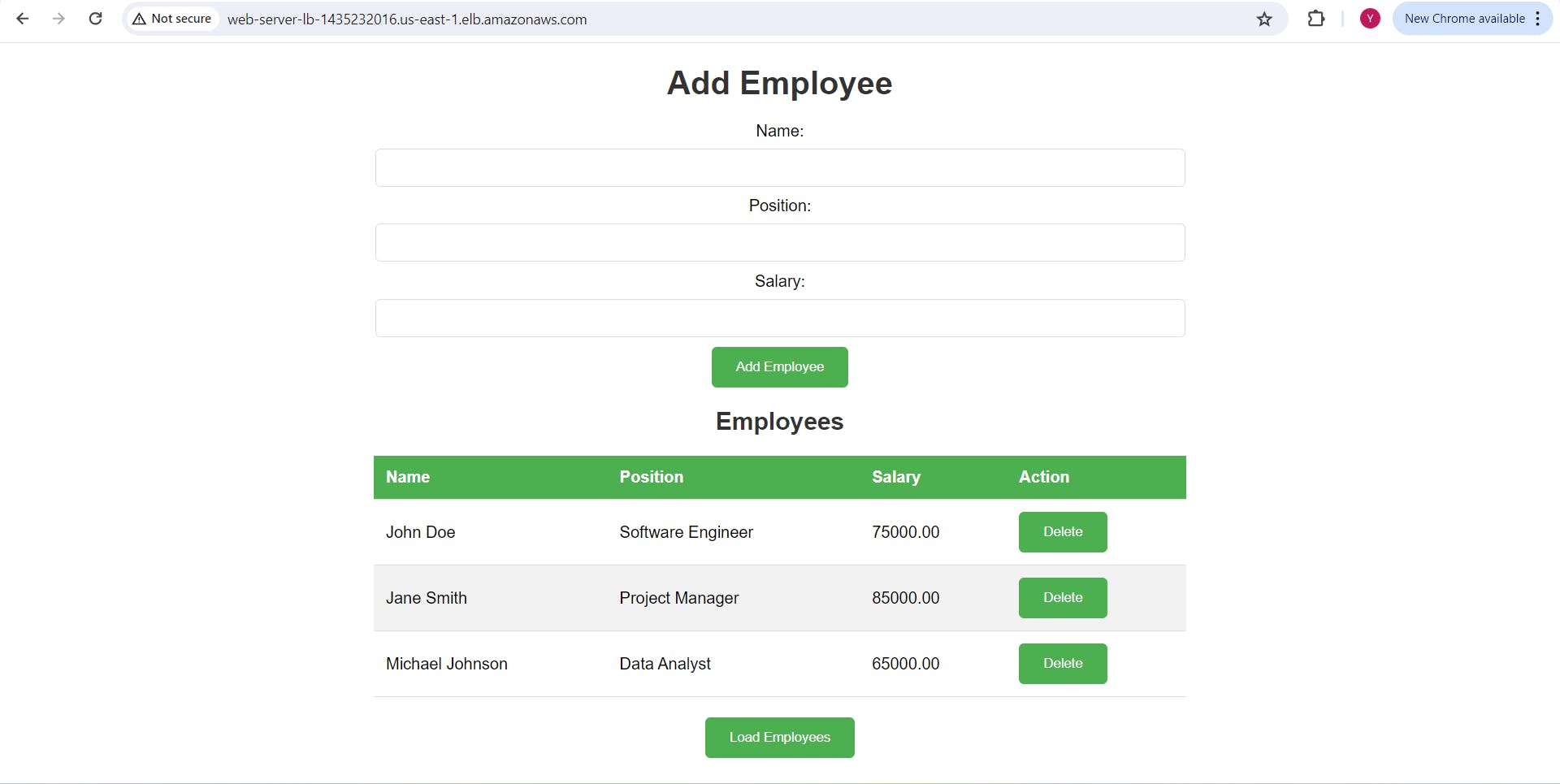
Congratulations! You have successfully deployed an application using a 3-tier architecture on AWS With ensuring scalability and high availability.